Traffic Forensics with Brim
Lab Note
The lab is provided by TryHackMe - Creators: heavenraiza & RussianPanda.
Link to access the lab: Masterminds (Free lab).
In this lab, we employ brim to perform traffic forensics. More info about brim can be found here.
Our goal is to answer the questions in Task 2, Task 3, and Task 4 of the lab.
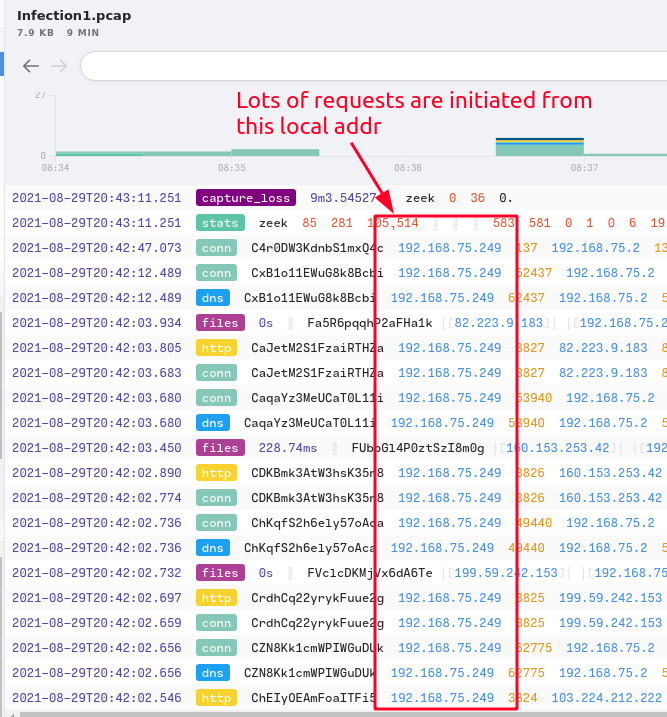
Task 2 - [Infection 1]
1. Provide the victim’s IP address.
Answer:
192.168.75.249.Query:
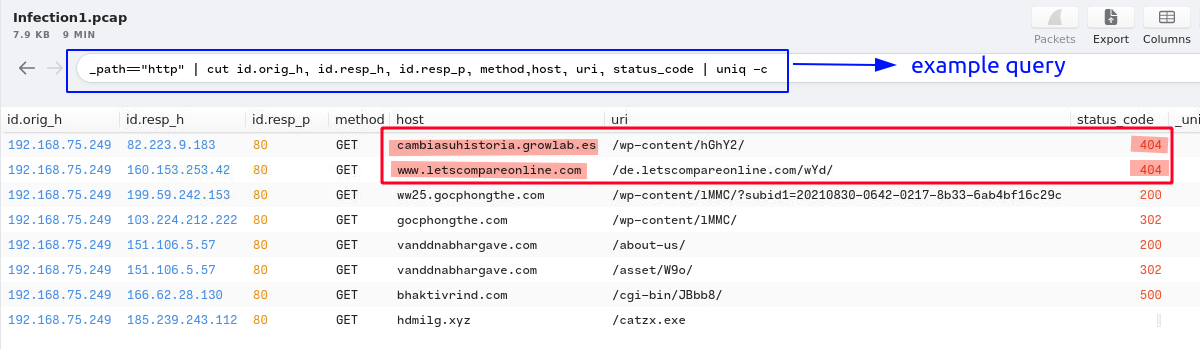
2. The victim attempted to make HTTP connections to two suspicious domains with the status ‘404 Not Found’. Provide the hosts/domains requested.
Answer:
cambiasuhistoria.growlab.es, www.letscompareonline.com.Query:
_path=="http" | cut id.orig_h, id.resp_h, id.resp_p, method,host, uri, status_code | uniq -c
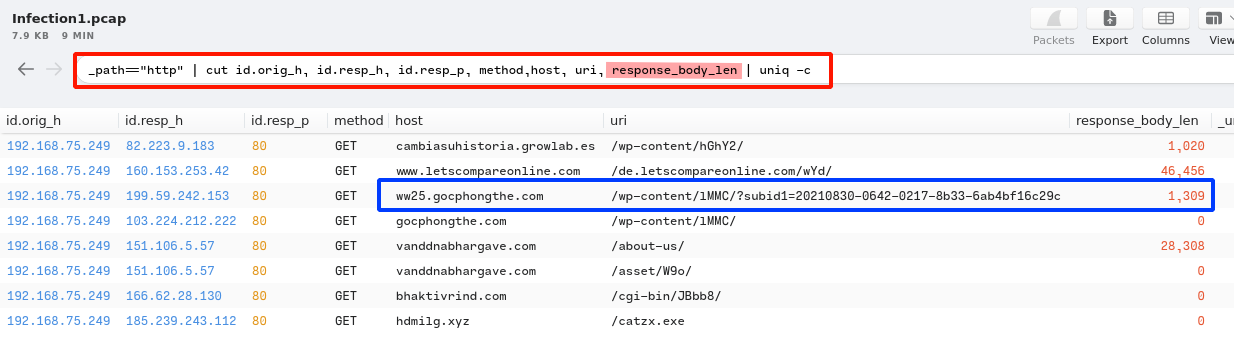
3. The victim made a successful HTTP connection to one of the domains and received the response_body_len of 1,309 (uncompressed content size of the data tr+ Answerferred from the server). Provide the domain and the destination IP address.
Answer:
ww25.gocphongthe.com,199.59.242.153.Query:
_path=="http" | cut id.orig_h, id.resp_h, id.resp_p, method,host, uri, response_body_len | uniq -c
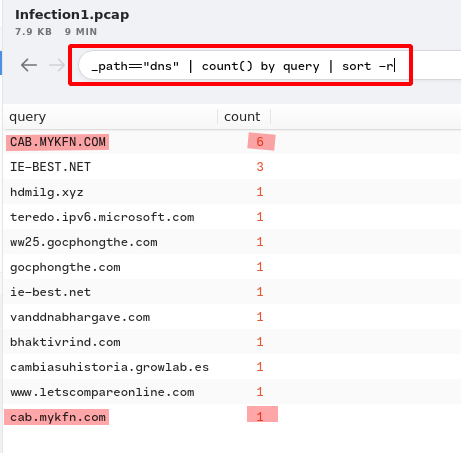
4. How many unique DNS requests were made to cab[.]myfkn[.]com domain (including the capitalized domain)?
Answer:
7Query:
_path=="dns" | count() by query | sort -r
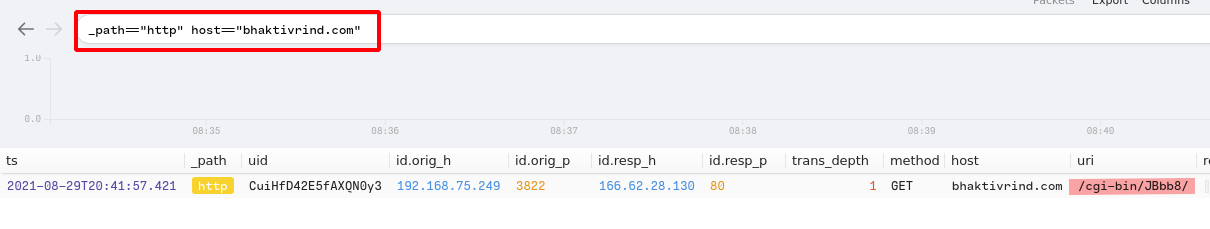
5.Provide the URI of the domain bhaktivrind[.]com that the victim reached out over HTTP.
Answer:
/cgi-bin/JBbb8/Query:
_path=="http" host=="bhaktivrind.com"
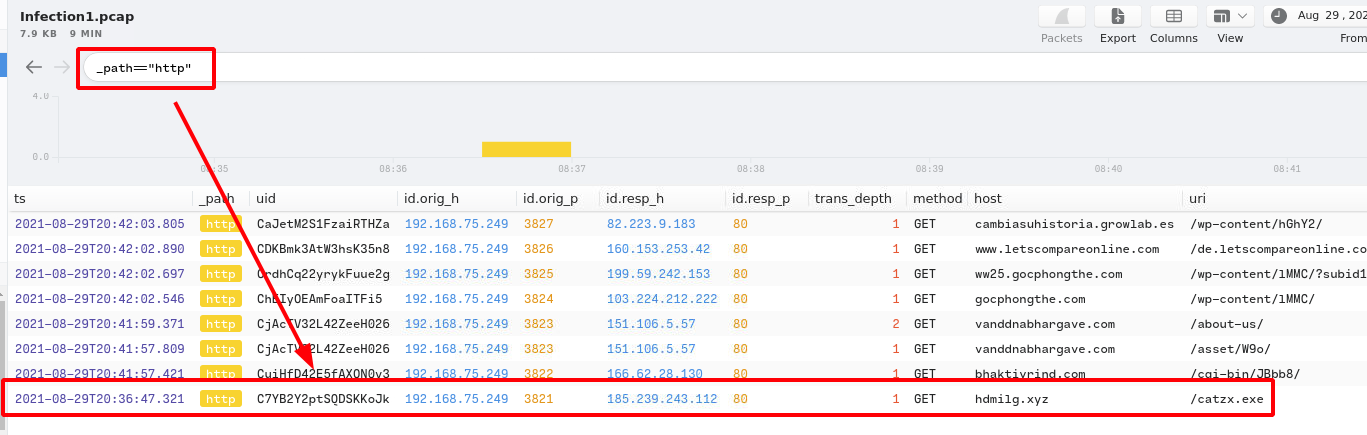
6. Provide the IP address of the malicious server and the executable that the victim downloaded from the server.
Answer:
185.239.243.112,catzx.exe.Query:
_path=="http"
7. Based on the information gathered from the second question, provide the name of the malware using VirusTotal.
- Answer:
Emotet
Task 3 - [Infection 2]
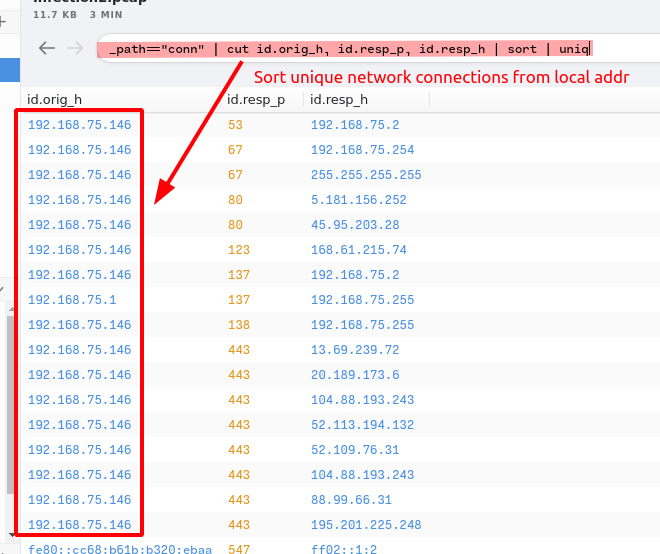
1. Provide the IP address of the victim machine.
Answer:
192.168.75.146Query:
_path=="conn" | cut id.orig_h, id.resp_p, id.resp_h | sort | uniq
2. Provide the IP address the victim made the POST connections to.
Answer:
5.181.156.252Query:
method=="POST" | cut ts, uid, id, method, uri, status_code
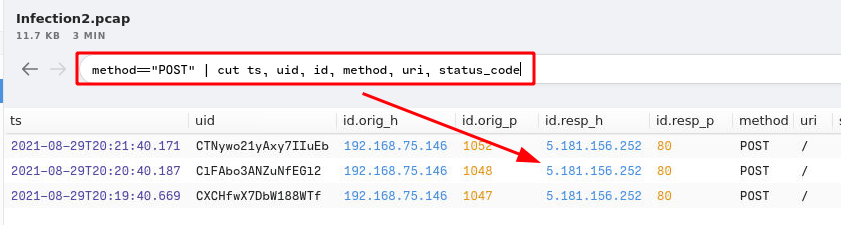
3. How many POST connections were made to the IP address in the previous question?
- Answer:
3
4. Provide the domain where the binary was downloaded from.
Answer:
hypercustom.topQuery:
_path=="http" | cut id.orig_h, id.resp_h, id.resp_p, method,host, uri | uniq -c
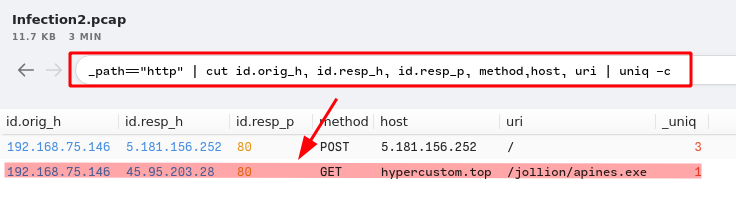
5. Provide the name of the binary including the full URI.
- Answer:
/jollion/apines.exe
6. Provide the IP address of the domain that hosts the binary.
- Answer:
45.95.203.28
7. There were 2 Suricata “A Network Trojan was detected” alerts. What were the source and destination IP addresses?
Answer:
192.168.75.146, 45.95.203.28Query:
event_type=="alert" | alerts := union(alert.category) by src_ip, dest_ip
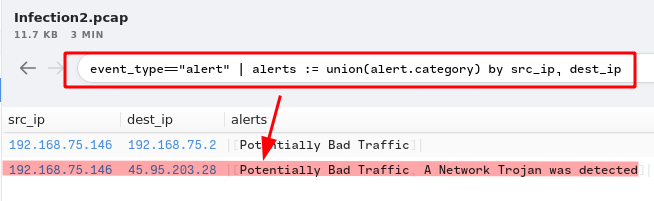
8. Taking a look at .top domain in HTTP requests, provide the name of the stealer (Trojan that gathers information from a system) involved in this packet capture using URLhaus Database.
- Answer:
Redline Stealer
Task 4 - [Infection 3]
1. Provide the IP address of the victim machine.
Answer:
192.168.75.232Query:
_path=="http" | cut id.orig_h, id.resp_h, id.resp_p, method,host, uri | uniq -c

2. Provide three C2 domains from which the binaries were downloaded (starting from the earliest to the latest in the timestamp)
Answer:
efhoahegue.ru,afhoahegue.ru,xfhoahegue.ruQuery:
_path=="http" | cut ts, id.orig_h, id.resp_h, id.resp_p, method,host, uri | uniq -c | sort ts
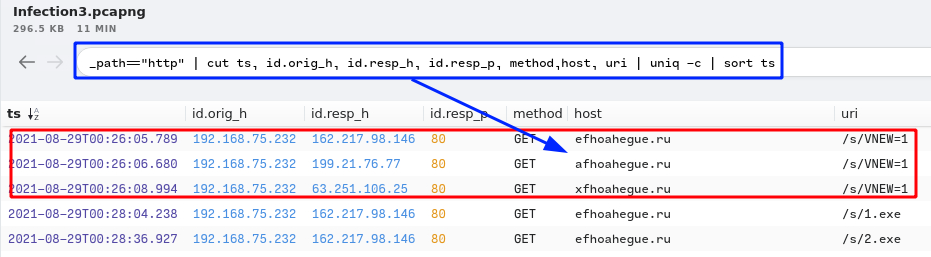
3. Provide the IP addresses for all three domains in the previous question.
- Answer:
162.217.98.146, 199.21.76.77, 63.251.106.25
4. How many unique DNS queries were made to the domain associated from the first IP address from the previous answer?
Answer:
2Query:
_path=="dns" query=="efhoahegue.ru"
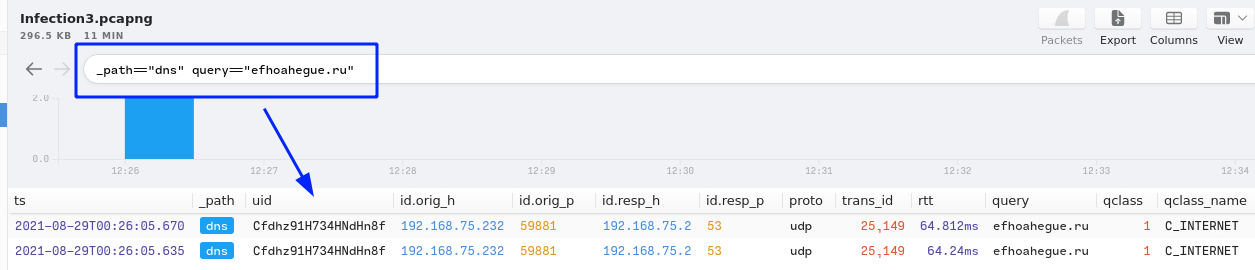
5. How many binaries were downloaded from the above domain in total?
Answer:
5Query:
_path=="http" host=="efhoahegue.ru"

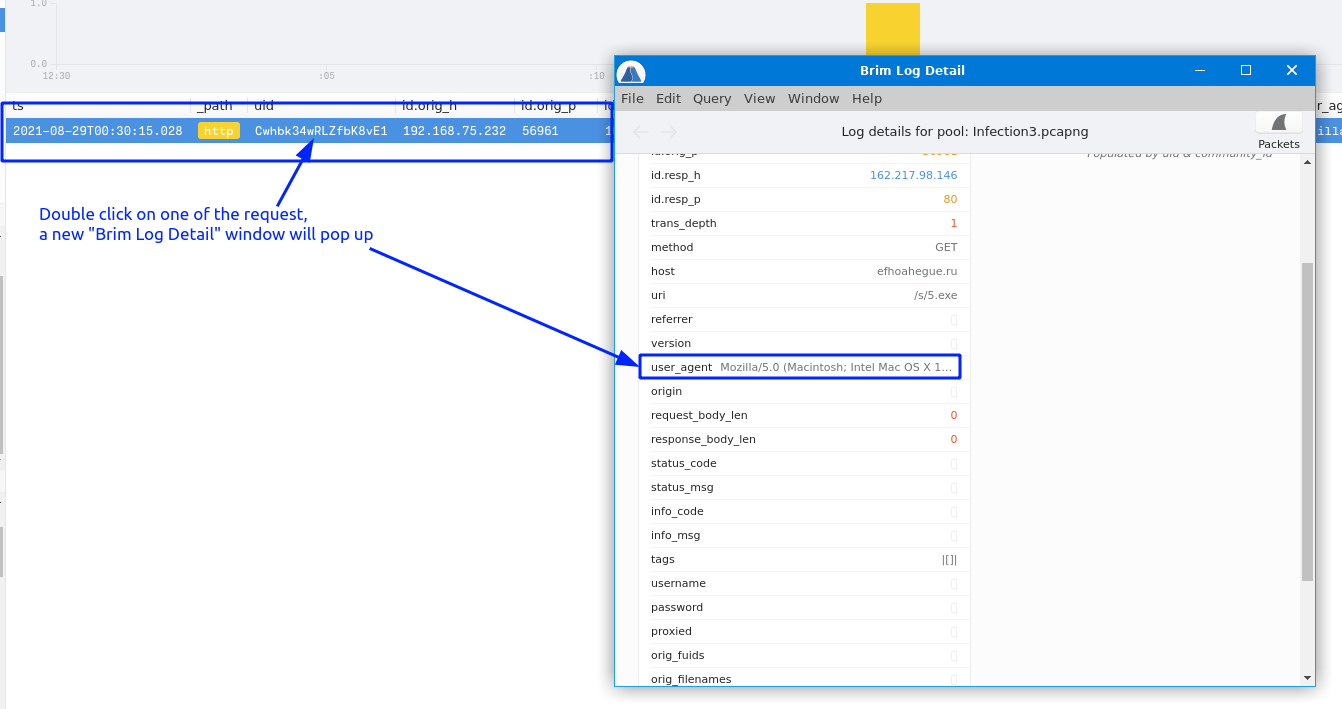
6. Provided the user-agent listed to download the binaries.
Answer:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10.9; rv:25.0) Gecko/20100101 Firefox/25.0Explanation:
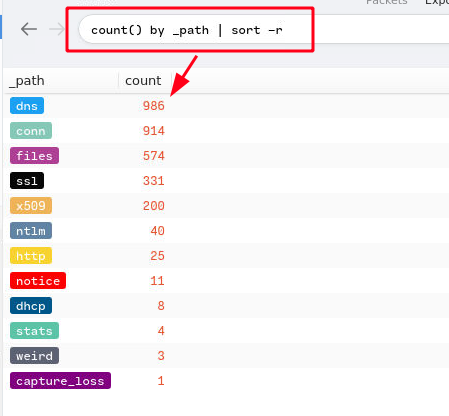
7. Provide the amount of DNS connections made in total for this packet capture.
Answer:
986Query:
count() by _path | sort -r
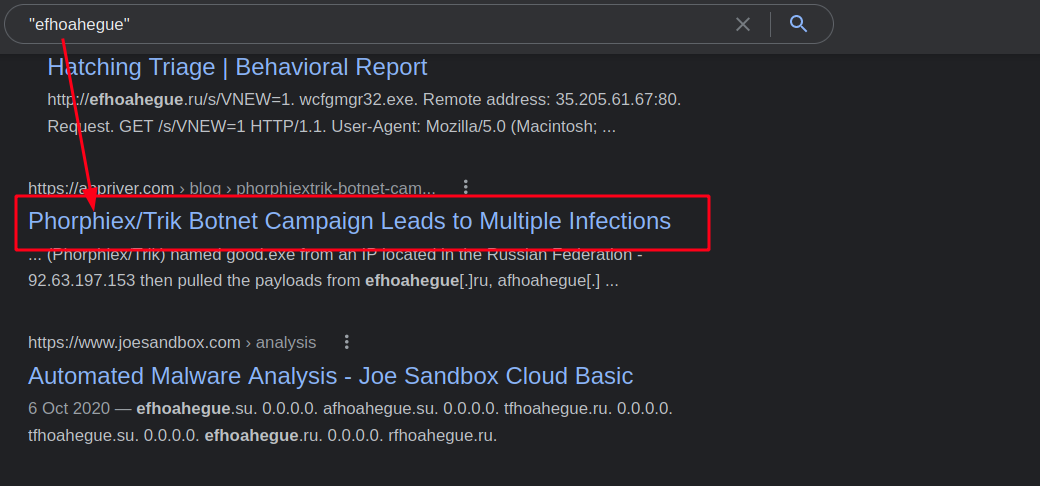
8. With some OSINT skills, provide the name of the worm using the first domain you have managed to collect from Question 2. (Please use quotation marks for Google searches, don’t use .ru in your search, and DO NOT interact with the domain directly).
Answer:
PhorphiexExplanation: