Magnitude EK II- Traffic Analysis
Description
Analyze the following packet and answer the questions.
- Link to download
.pcap: here. (Password:infected)
Credit: malware-traffic-analysis.net.
Question
For each pcap, answer the following questions:
1) What is the date and time of the activity?
2) What is the IP address of the Windows host that gets infected?
3) What is the domain name and IP address of the compromised web site?
4) What is the domain name and IP address that delivered the exploit kit (EK)?
5) What is the name of the EK?
Rationale
[1]. What is the date and time of the activity?
2015-01-04 15:27:20
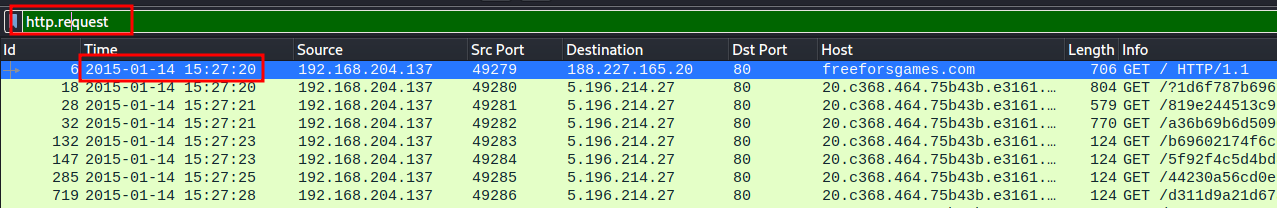
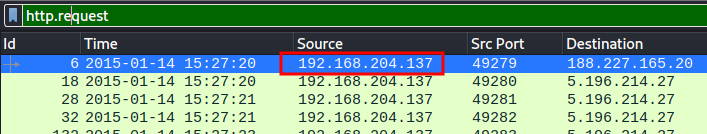
[2]. What is the IP address of the Windows host that gets infected?
192.168.204.137
[3]. What is the domain name and IP address of the compromised web site?
- Domain name:
freeforsgames.com. - IP Address:
188.227.165.20.
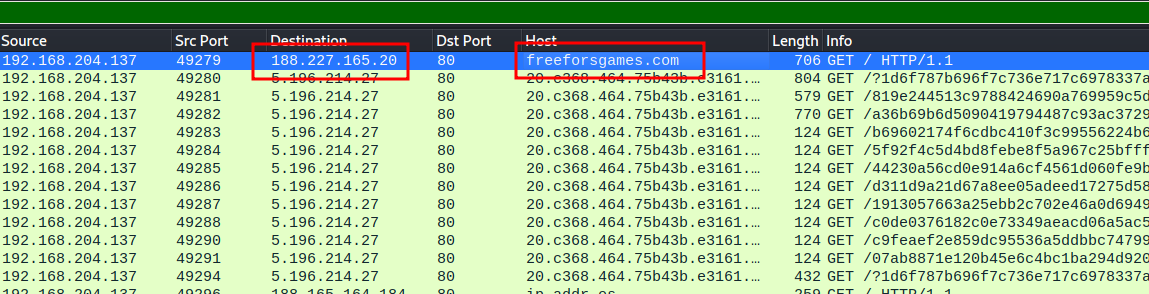
- It redirects the victim to the EK site.
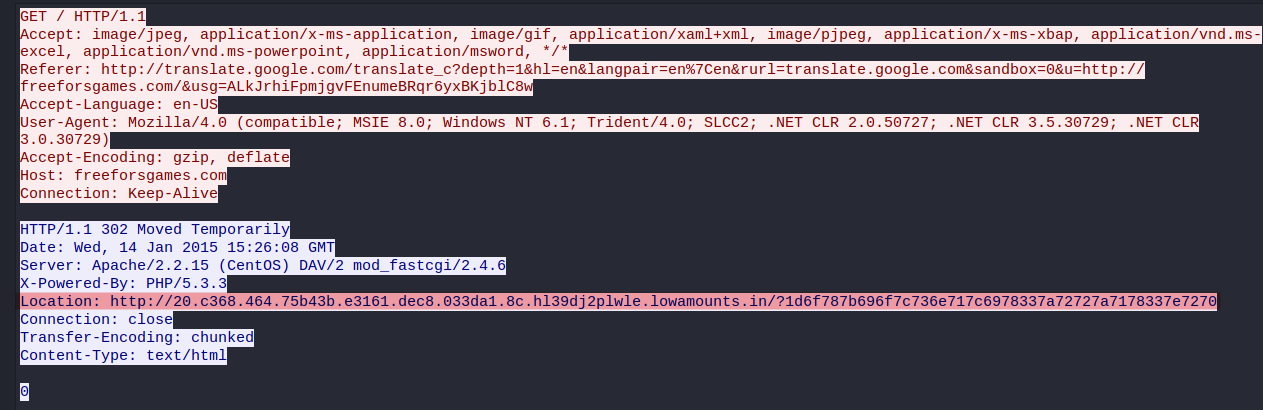
[4]. What is the domain name and IP address that delivered the exploit kit (EK)?
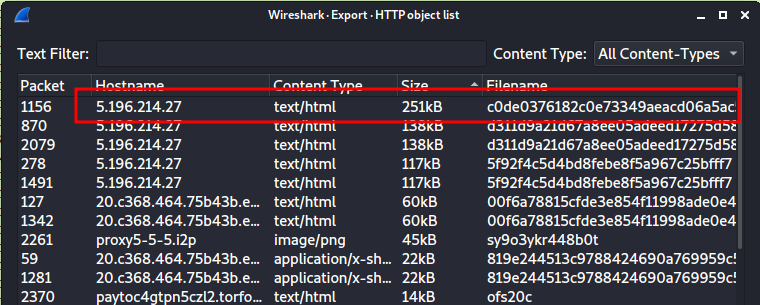
- Domain name:
20.c368.464.75b43b.e3161.dec8.033da1.8c.hl39dj2plwle.lowamounts.in
IP Address:
5.196.214.27.This is an EK website due to a chain of infections happening here. Also this website delivered a large size of payload.
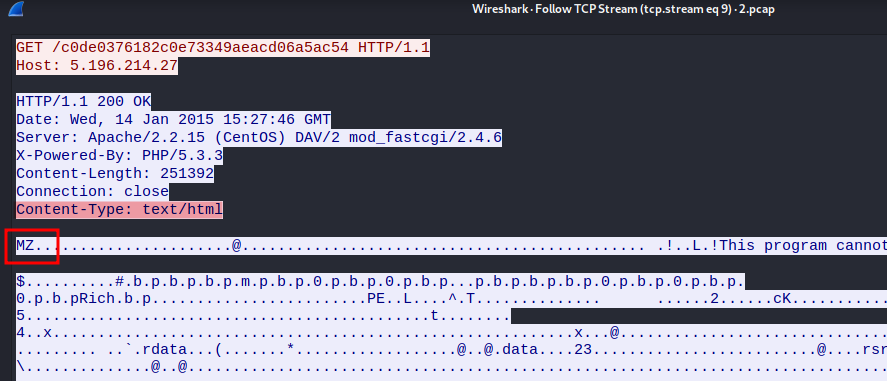
- Inspecting the payload, we can see that the
Content-Typeheader ishtml, but the body is Windows’s.exe.
[5]. What is the name of the EK?
Magnitude EK
Analyse the traffic with Suricata
- On the terminal, we execute the following command:
$ suricata -l suricata2 -c /etc/suricata/suricata.yaml -r 2.pcap -v
25/9/2021 -- 19:02:02 - <Notice> - This is Suricata version 6.0.3 RELEASE running in USER mode
25/9/2021 -- 19:02:02 - <Info> - CPUs/cores online: 4
...
- Inspecting the
fast.logfile, we detect aNetwork Trojanclaimed by multiple rules.
$ head -10 suricata2/fast.log
01/14/2015-10:27:28.580695 [**] [1:2009897:17] ET MALWARE Possible Windows executable sent when remote host claims to send html content [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 5.196.214.27:80 -> 192.168.204.137:49286
01/14/2015-10:27:34.974606 [**] [1:2020105:3] ET POLICY Possible IP Check ip-addr.es [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 192.168.204.137:49296 -> 188.165.164.184:80
01/14/2015-10:27:28.843465 [**] [1:2018959:4] ET POLICY PE EXE or DLL Windows file download HTTP [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 5.196.214.27:80 -> 192.168.204.137:49286
01/14/2015-10:27:28.843465 [**] [1:2016538:3] ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 5.196.214.27:80 -> 192.168.204.137:49286
01/14/2015-10:27:28.843465 [**] [1:2021076:2] ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 5.196.214.27:80 -> 192.168.204.137:49286
01/14/2015-10:27:36.757315 [**] [1:2014726:127] ET POLICY Outdated Flash Version M1 [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.204.137:49301 -> 5.196.214.27:80
01/14/2015-10:27:36.757746 [**] [1:2031747:1] ET HUNTING Observed Interesting Content-Type Inbound (application/x-sh) [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 5.196.214.27:80 -> 192.168.204.137:49301
01/14/2015-10:27:30.413374 [**] [1:2009897:17] ET MALWARE Possible Windows executable sent when remote host claims to send html content [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 5.196.214.27:80 -> 192.168.204.137:49288
01/14/2015-10:27:30.674478 [**] [1:2018959:4] ET POLICY PE EXE or DLL Windows file download HTTP [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 5.196.214.27:80 -> 192.168.204.137:49288
01/14/2015-10:27:30.674478 [**] [1:2016538:3] ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download [**] [Classification: Potentially Bad Traffic] [Priority: 2] {TCP} 5.196.214.27:80 -> 192.168.204.137:49288
Analyse the traffic with Snort
$ sudo snort -c /etc/nsm/securityonion-eth0/snort.conf -r 2.pcap --daq pcap -k none -q -A console
01/14-15:27:21.493706 [**] [1:2014726:98] ET POLICY Outdated Flash Version M1 [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {TCP} 192.168.204.137:49281 -> 5.196.214.27:80
01/14-15:27:21.493706 [**] [1:2020895:5] ET CURRENT_EVENTS Magnitude Flash Exploit (IE) M2 [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 192.168.204.137:49281 -> 5.196.214.27:80
01/14-15:27:21.493706 [**] [1:2019799:2] ET CURRENT_EVENTS Magnitude Flash Exploit (IE) [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 192.168.204.137:49281 -> 5.196.214.27:80