Boss Of The SOC (BOTS) v1 - Threat Hunting with Splunk (II)
Description
- The lab is provided by INE - Effectively Using Splunk (S1).
- Another very good & free lab: here.
Continuing of Boss Of The SOC (BOTS) v1 - Threat Hunting with Splunk (I) …
Step 4 - Exploitation Activities
In this phase, we’ll employ Splunk to uncover any exploitation activity on the network. Let’s us focus on stream:http sourcetype. The query is:
index=botsv1 sourcetype="stream:http"
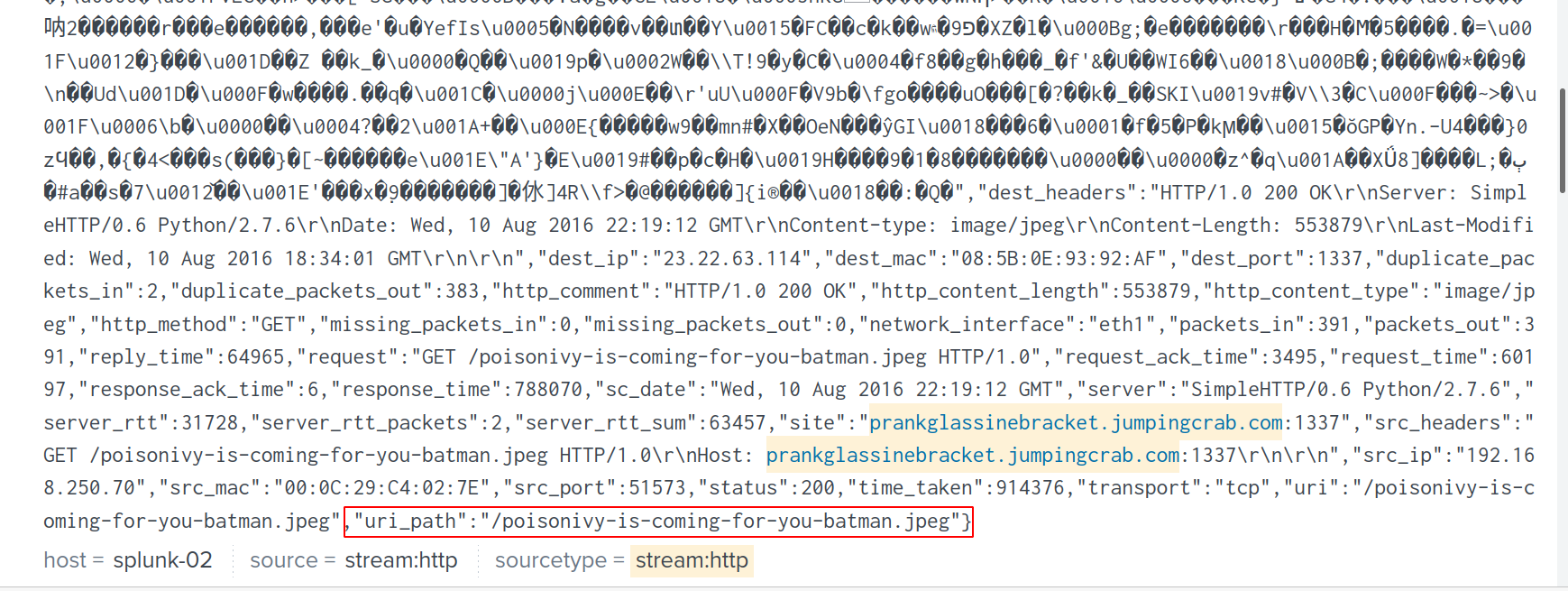
Considering the following image:
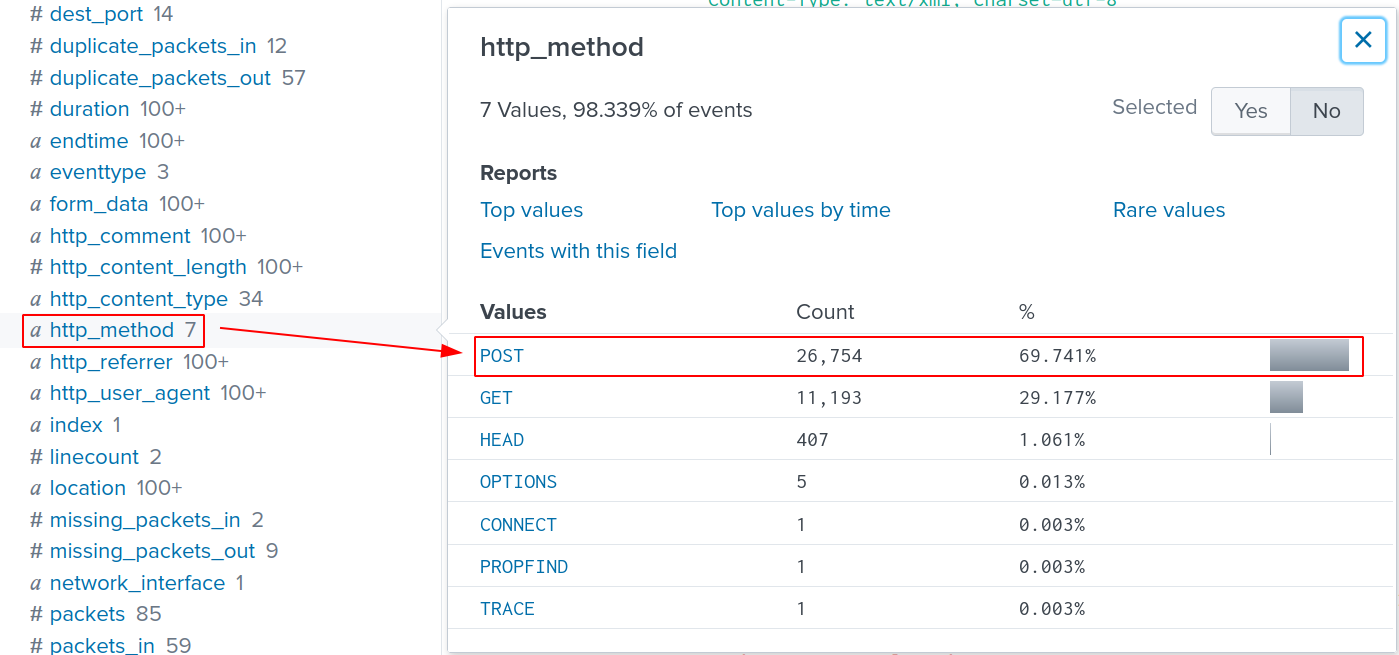
Looking at http_method section in the INTERESTING FIELDS column, it’s obvious that POST requests account for a large portion of HTTP requests.
We are also interested in the requests being sent to 192.168.250.70, which is our organization website. The search we use is as the following.
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix"
Note: NOT "Acunetix" is specified to exclude Acunetix scanner requests.
Applying the search, the result is much cleaner. Let’s look at the http_user_agent field.
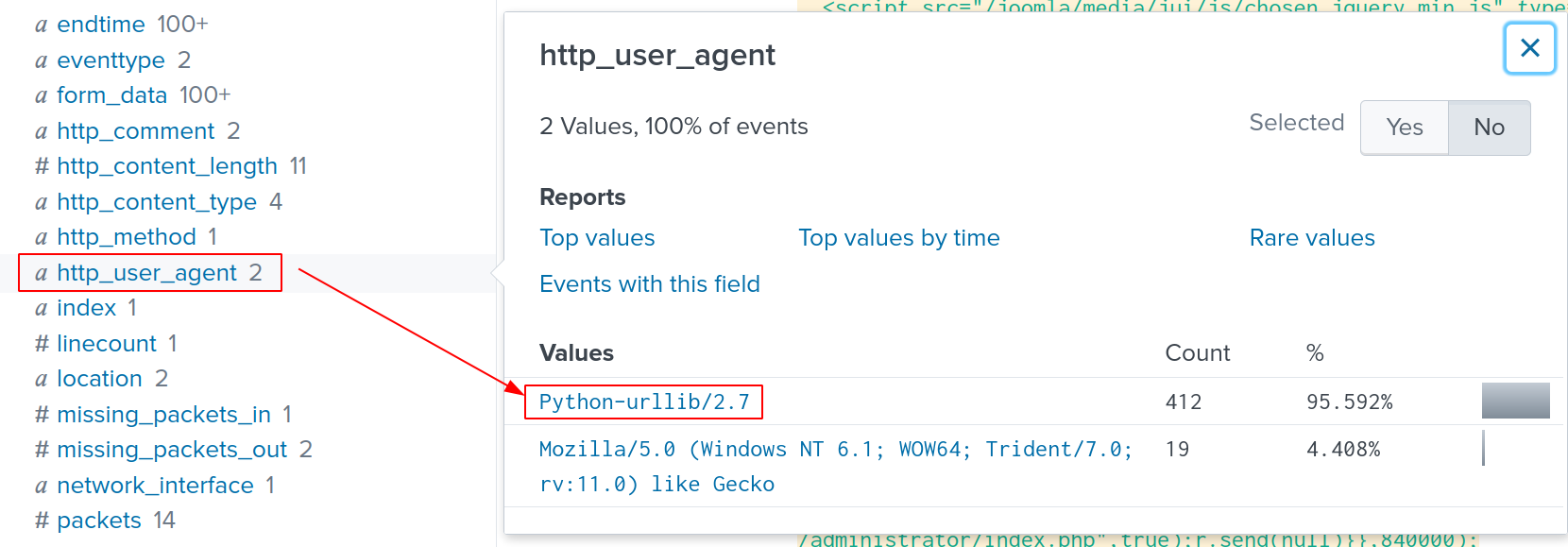
We discovered that the agent Python-urllib/2.7 is used, let’s also include it in our search.
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix" http_user_agent="Python*"
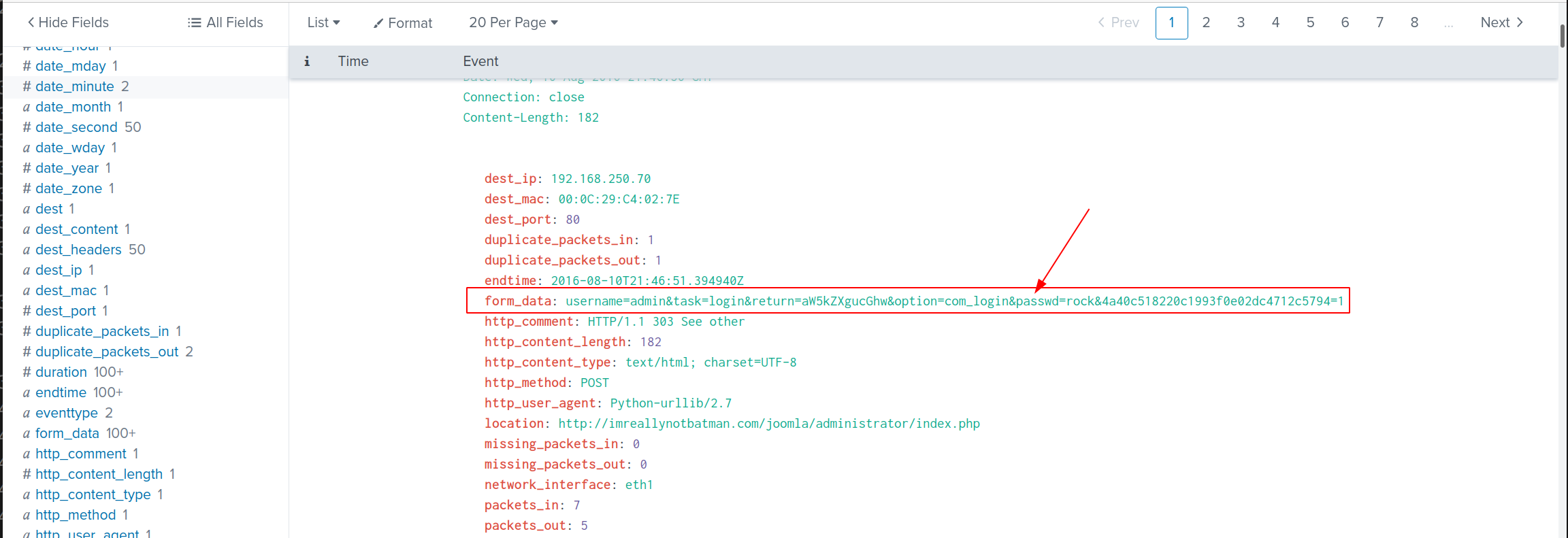
Scroll down a little bit, we can see that the form_data contains values of username and password!
Considering the below query:
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix" http_user_agent="Python*" | table _time,form_data,c_ip | sort + _time
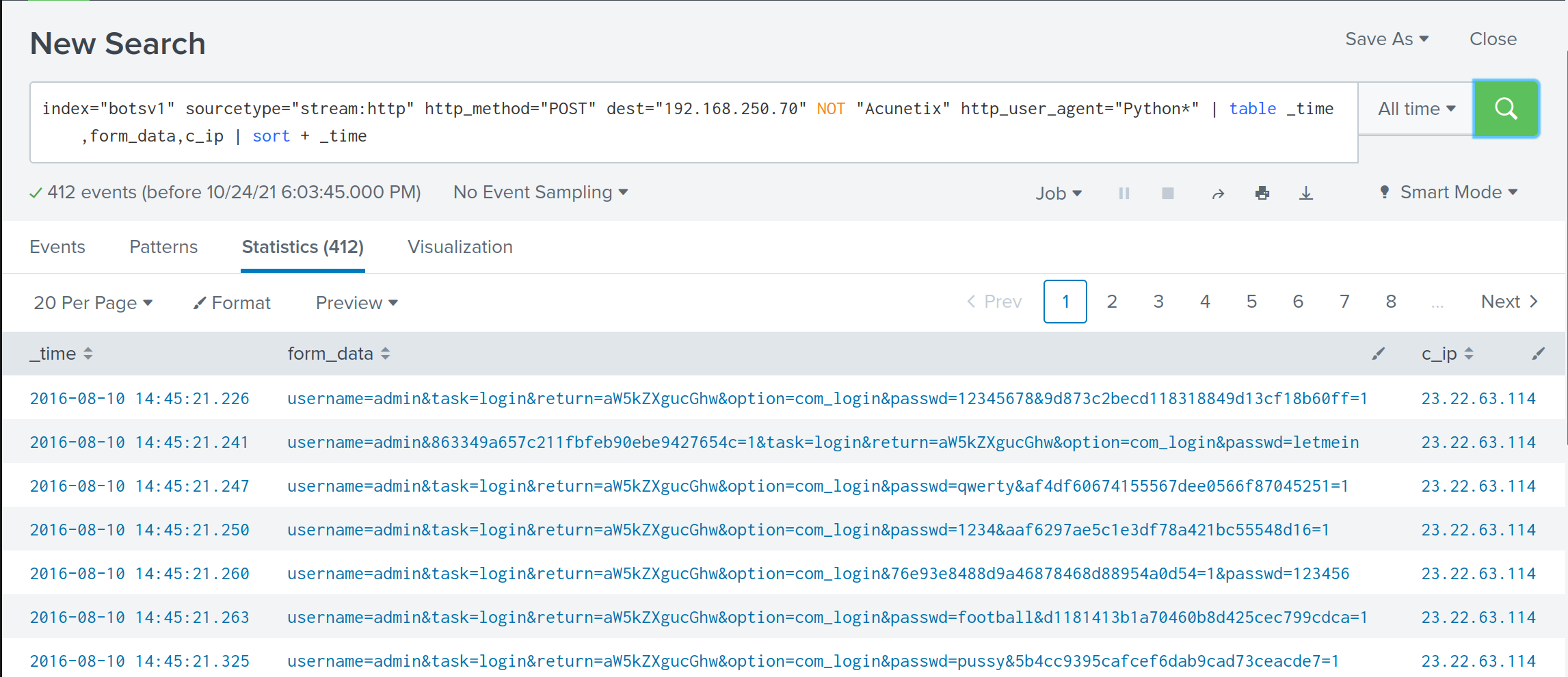
It’s undoubtable that the APT performed password bruteforcing. If we are interested in checking whether the attack is successful, the User Agent can tell us.
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix" | search form_data="*user*pass*" http_user_agent="Mozilla*" | table _time,form_data,http_user_agent,c_ip | sort + _time
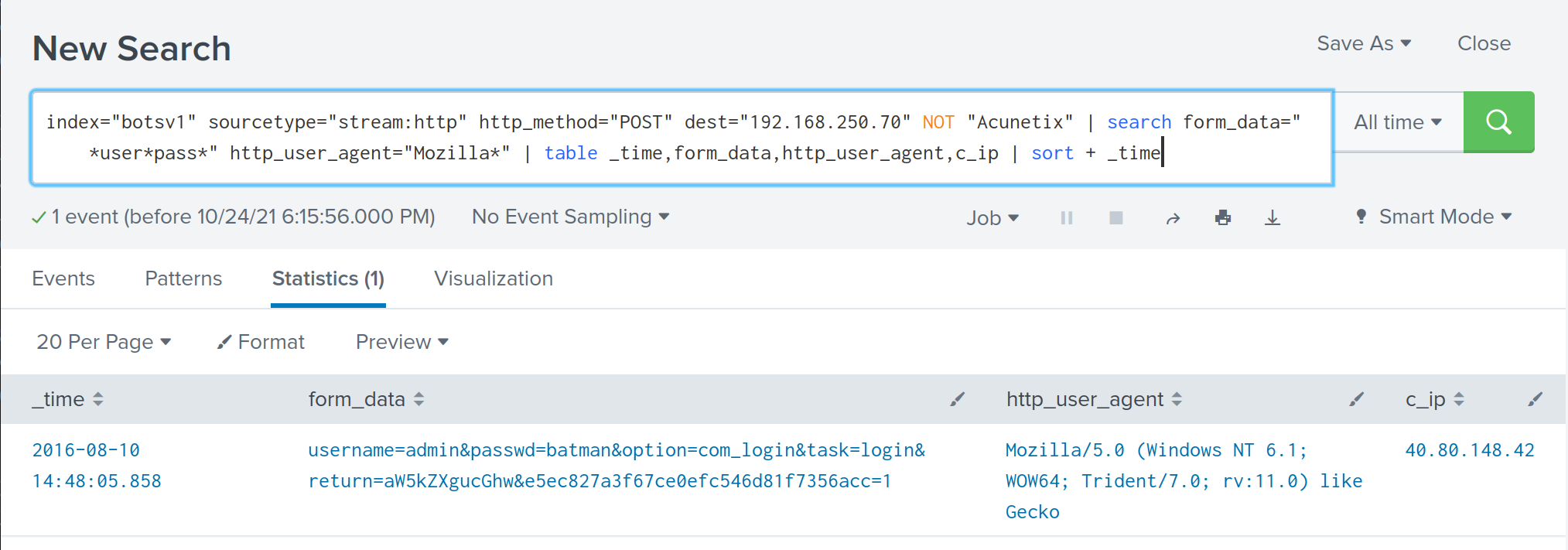
It’s very likely that batman is the correct password. The search revealed that attackers used Python to bruteforce password then logged in with their actual web browser.
Finally, if we want to see the timeframe of the two successful logins, we can do so as belows:
index="botsv1" sourcetype="stream:http" http_method="POST" dest="192.168.250.70" NOT "Acunetix" | search form_data="*passwd=batman*" | table _time,form_data,http_user_agent,c_ip | sort + _time
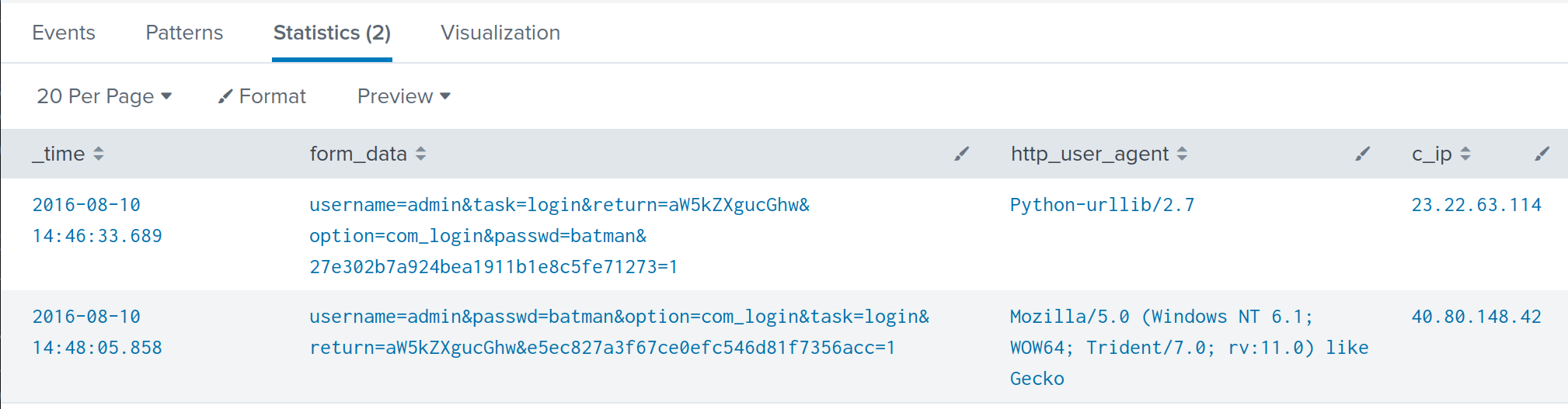
The meaningful timeframe can also explain a successful bruteforce attack.
Step 5 - Installation Activities
As far as the exploitation is successful, we are mostly interested in the malware being transferred to the victim.
To upload the malware, we want to look at POST request with the extension of a Windows executable.
index=botsv1 NOT "Acunetix" sourcetype=stream:http http_method=POST dest=192.168.250.70 ".exe"
part_filename{} is the field we want to look at, but it’s not enabled by default. We will simply click on All Fields, then choose part_filename to activate it.
By doing so, we can efficiently extract files are uploaded to the server as the following image:
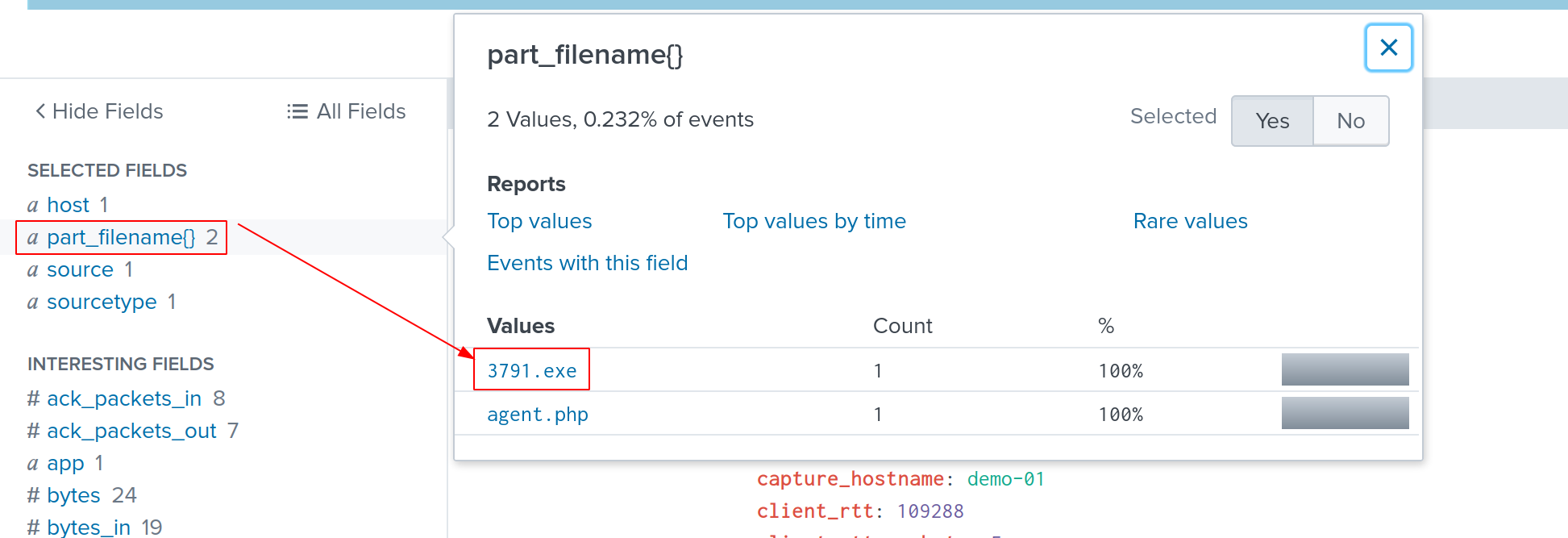
The file 3791.exe is malicious due to the source address.
Splunk provides the ability to extract hashes of the uploaded files. To do that, we focus on Sysmon log events:
index=botsv1 sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational"
We can narrow down the search by looking at the executable 3791.exe and Event ID is 1.
index=botsv1 3791.exe sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=1
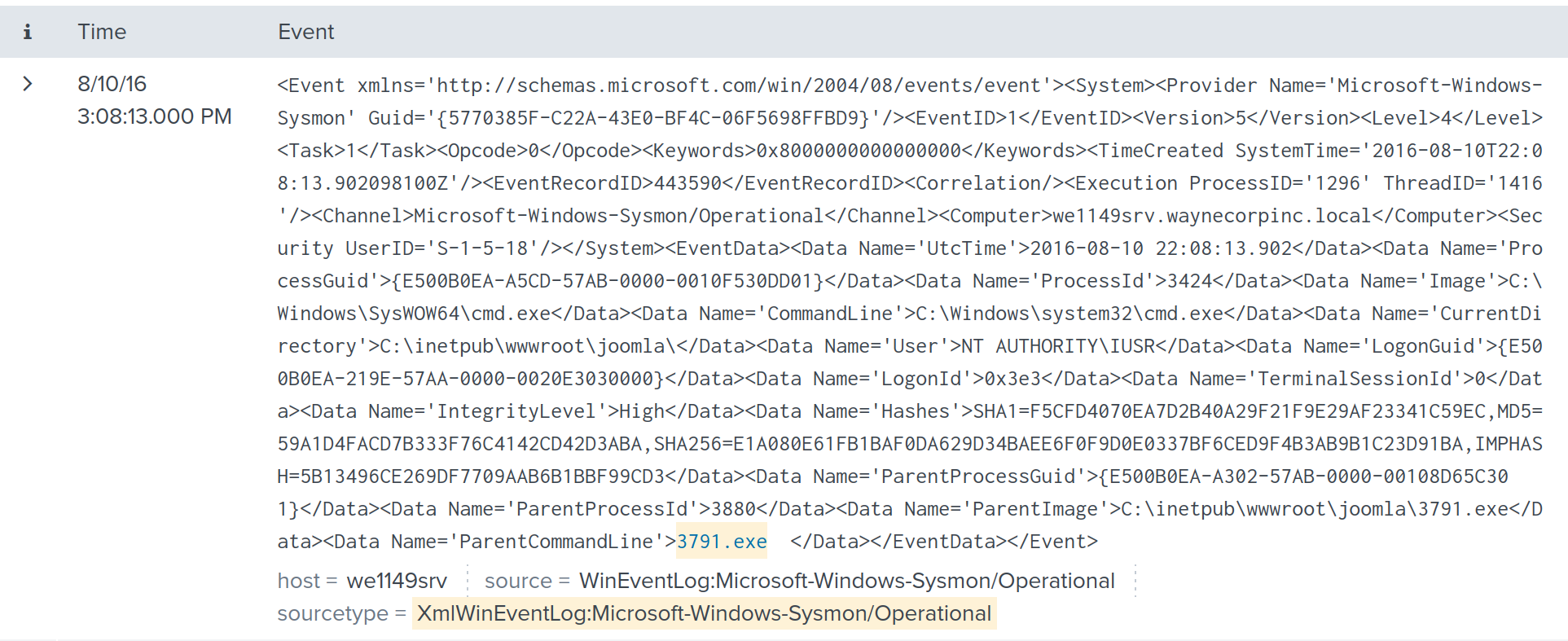
We can make an additional step by adding CommandLine to only filter the commands initiated from 3791.exe.
index=botsv1 "3791.exe" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=1 CommandLine=3791.exe
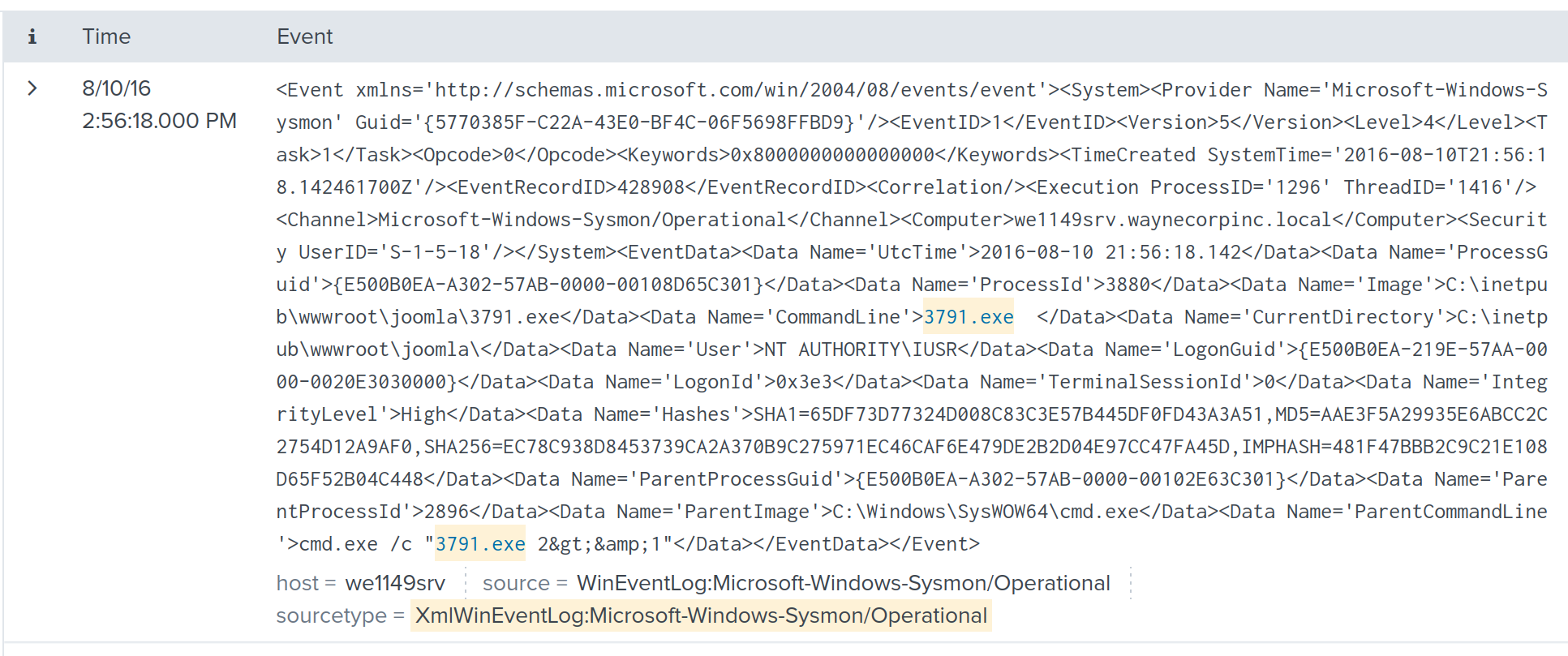
In order to extract the relevant hash, we can do as follows:
index=botsv1 "3791.exe" sourcetype="XmlWinEventLog:Microsoft-Windows-Sysmon/Operational" EventCode=1 CommandLine=3791.exe | stats values(md5)
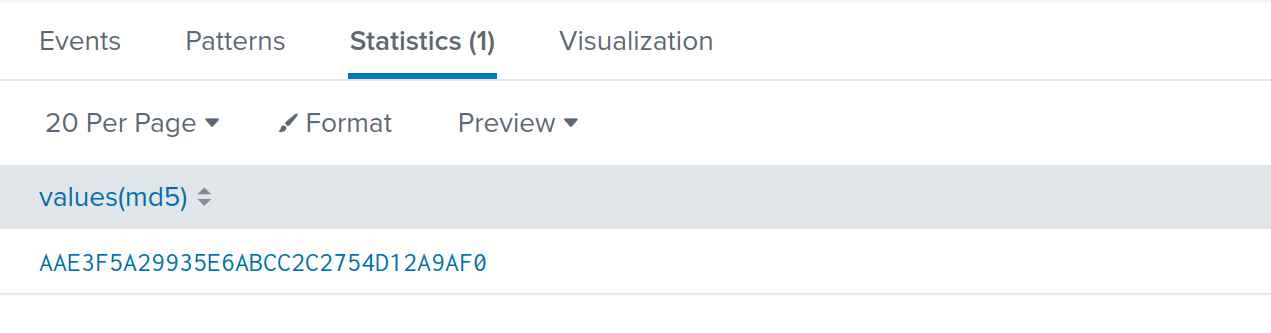
We then submit the hash onto www.hybrid-analysis.com, it’s marked as malicious.
Step 6 - Command and Control Server
In this phase, the APT will mostly interact with the victim over C2. It’s very likely that C2 will use domain to interact with the victim.
Splunk allows us to extract domains with stream:dns sourcetype. Let’s us filter DNS traffic of the 22.23.63.114 ip address.
index=botsv1 sourcetype=stream:dns "23.22.63.114" | stats values(name{})
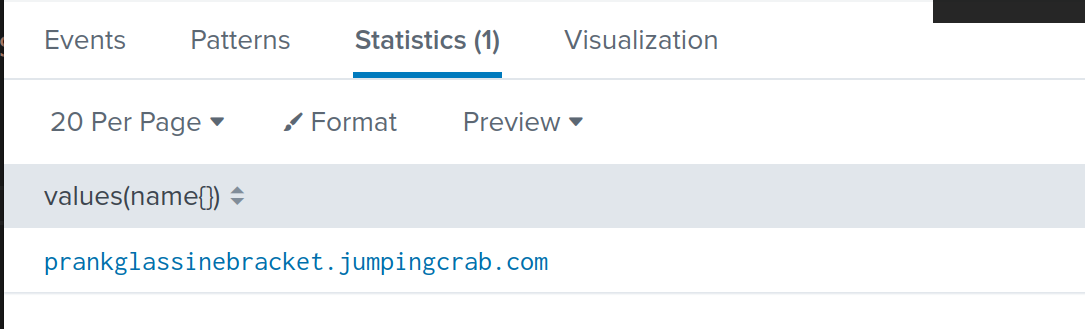
If we look a bit closer, this domain defaces our webserver.
index=botsv1 sourcetype="stream:http" "prankglassinebracket.jumpingcrab.com"