Boss Of The SOC (BOTS) v1 - Threat Hunting with Splunk (I)
Description
- The lab is provided by INE - Effectively Using Splunk (S1).
- Another very good & free lab: here.
In this post, we’ll proactively hunt for Cyber Attack Kill Chain from BOTsv1 dataset using Splunk.
Step 1 - Reconnaissance
Our organization’s website is imreallynotbatman.com.
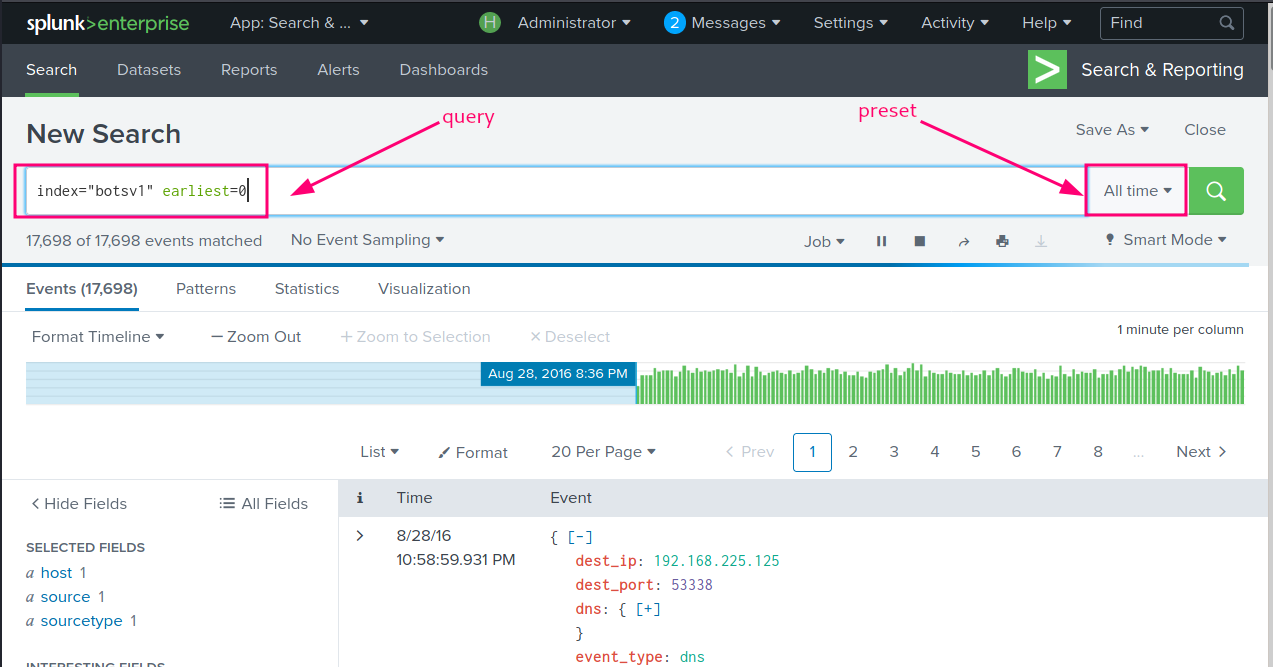
To begin with, we’ll test if Splunk can access the ingested data by submitting the following query:
index="botsv1" earliest=0with thePreset: All time.
We should be able to see the events are adding on as time progesses.
Now, let’s us identify traffic related to the imreallynotbatman.com website. This can be achieved via the below query:
index="botsv1" imreallynotbatman.com
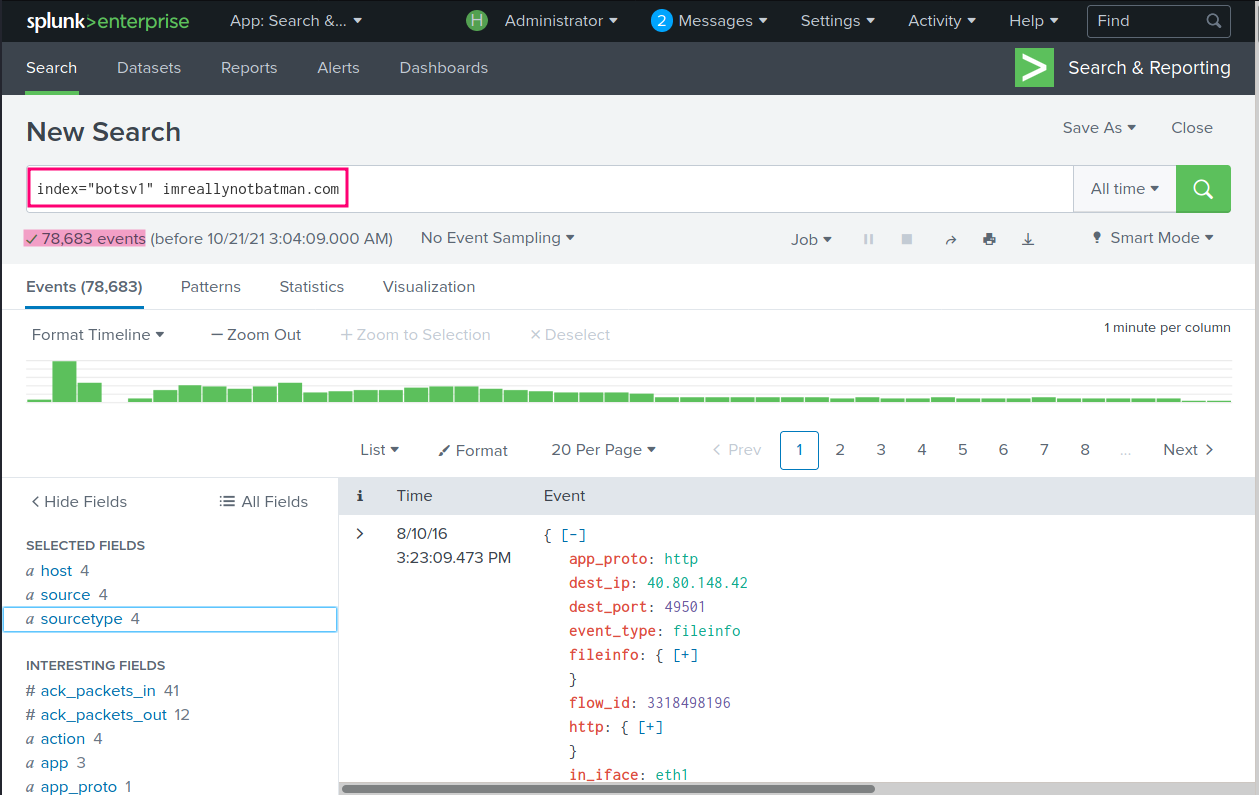
There are 78,683 events relating to this website. Currently, not all of them are essential to us, we want to narrow down those events to single stream.
We can observe relevant streams as the following:
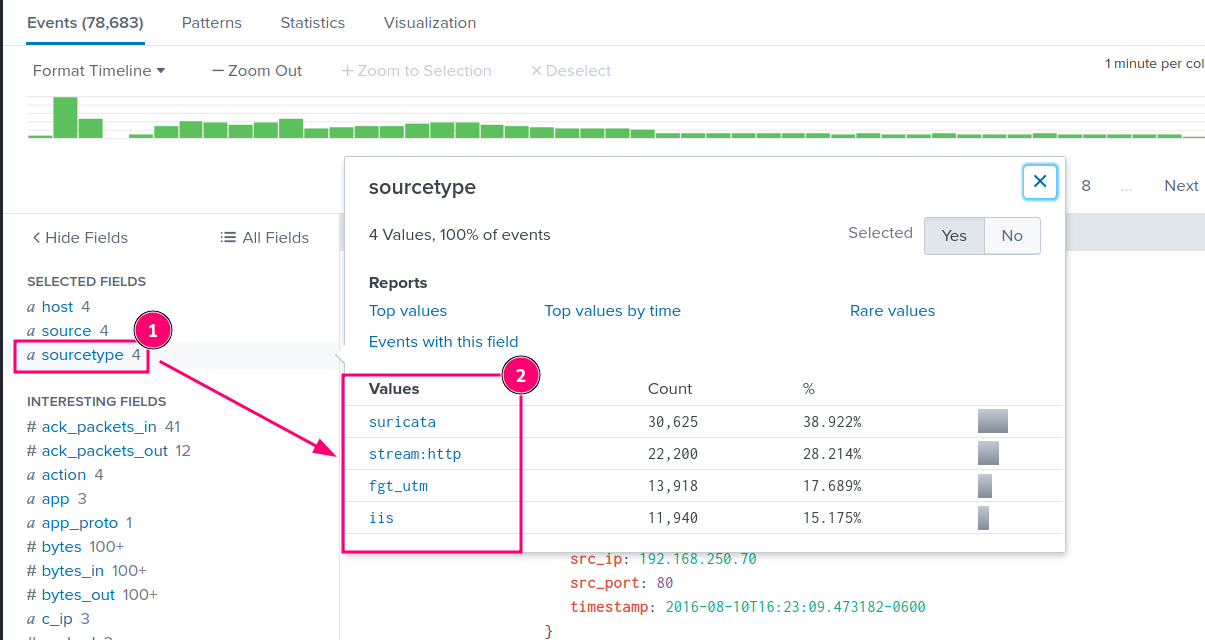
sourcetype of stream:http is definitely interesting to us, the others are also valuable to check out. For now, we concentrate on the HTTP traffic.
In order to list HTTP streams, we submit the below query:
index="botsv1" sourcetype="stream:http" imreallynotbatman.com
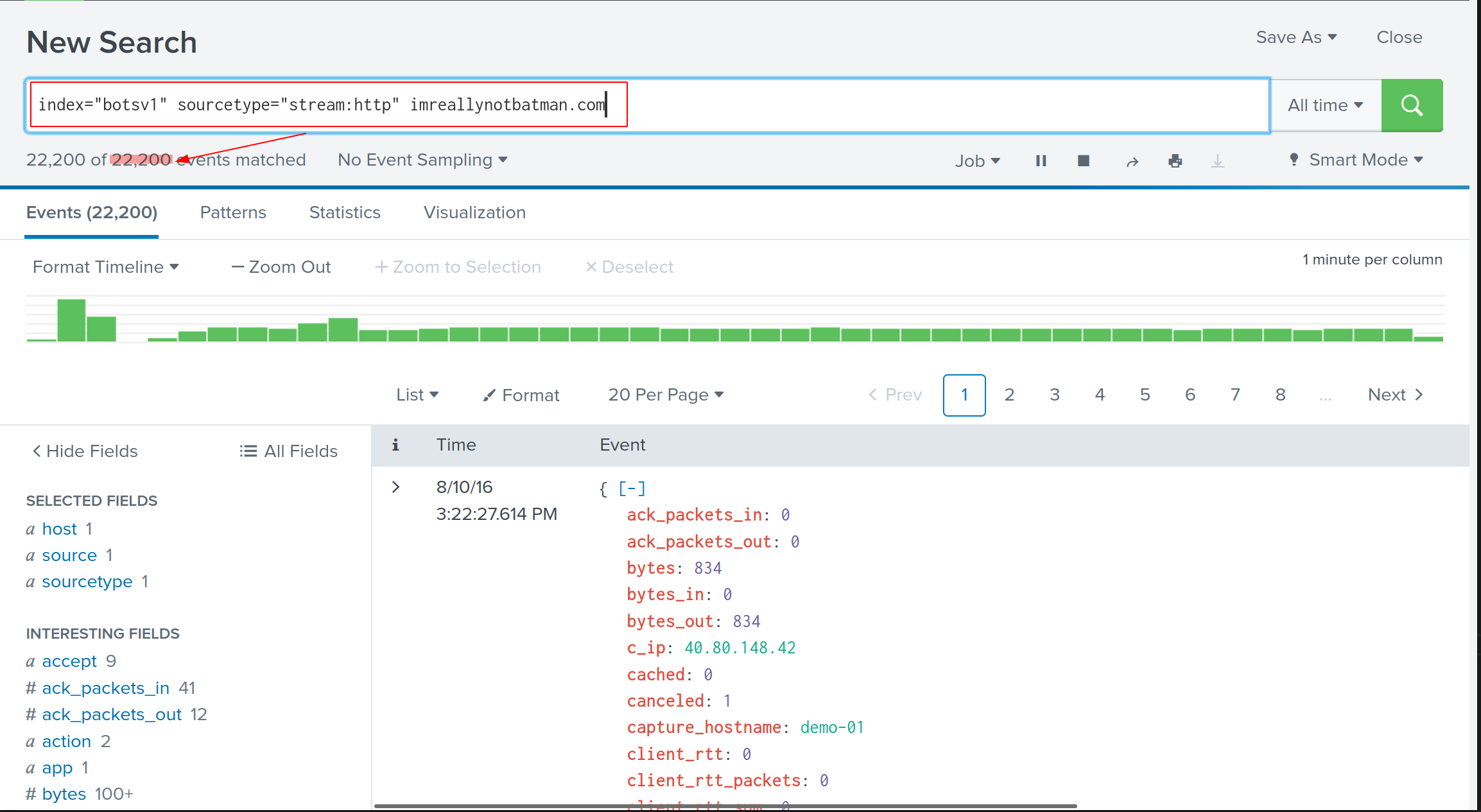
From the outputs, events are brought down to a decent figure, Yet, it’s still too overwhelming to inspect those traffic manually.
Good for us, Splunk is able to sort unique IP addresses. Therefore, we can start investigating the traffic accounting for a large number of requests.
The query we use here is very similar to the previous one. By adding ... | fields src_ip, we can extract unique source ip address.
index="botsv1" sourcetype="stream:http" imreallynotbatman.com | fields src_ip
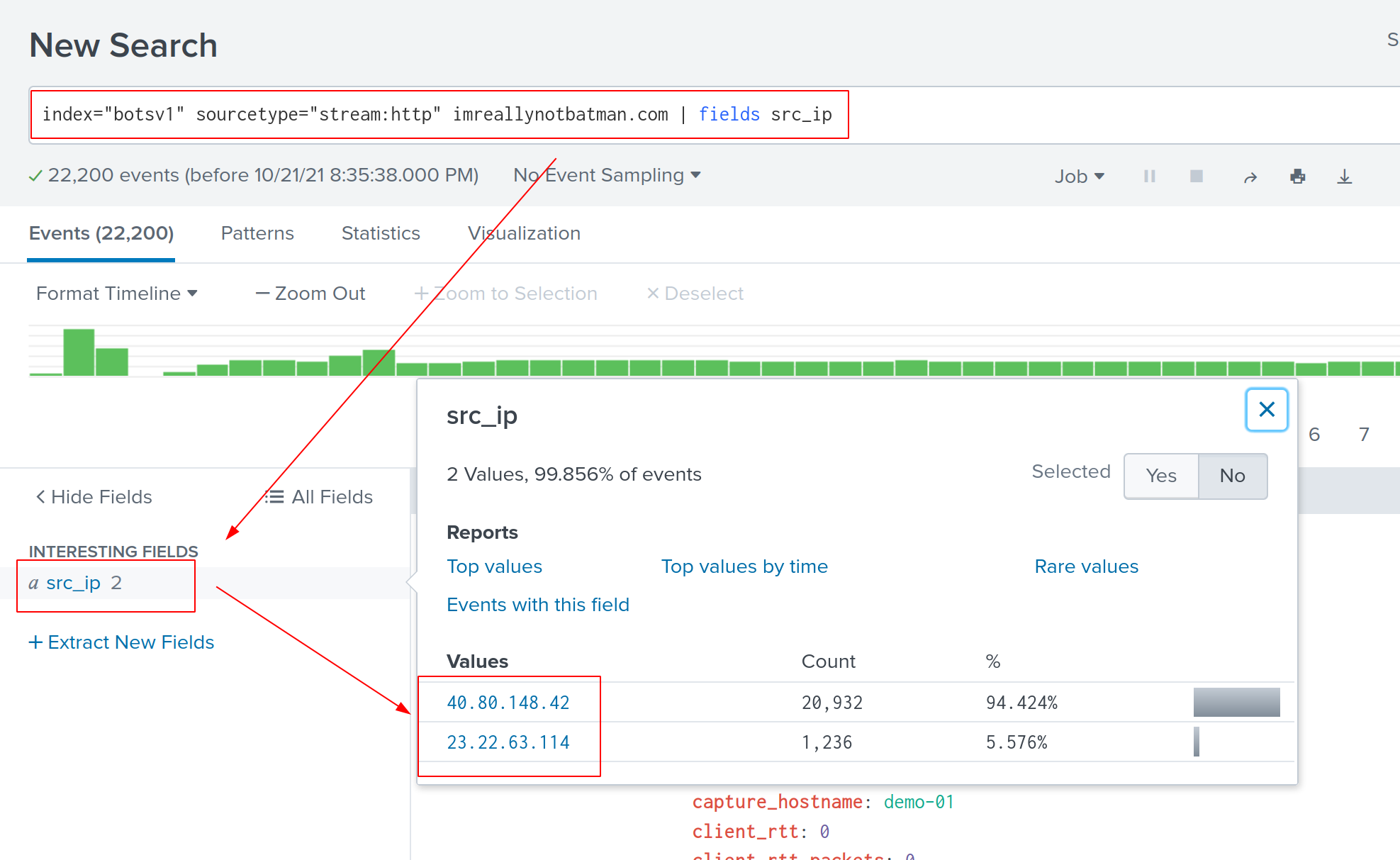
The addresses - 40.80.148.42 and 23.22.63.114 involved in most parts of the HTTP stream. Additionally, there is another approach we can use to count the traffic.
index="botsv1" sourcetype="stream:http" imreallynotbatman.com | stats count(src_ip) as "Source IP" by src_ip | sort + "Source IP"
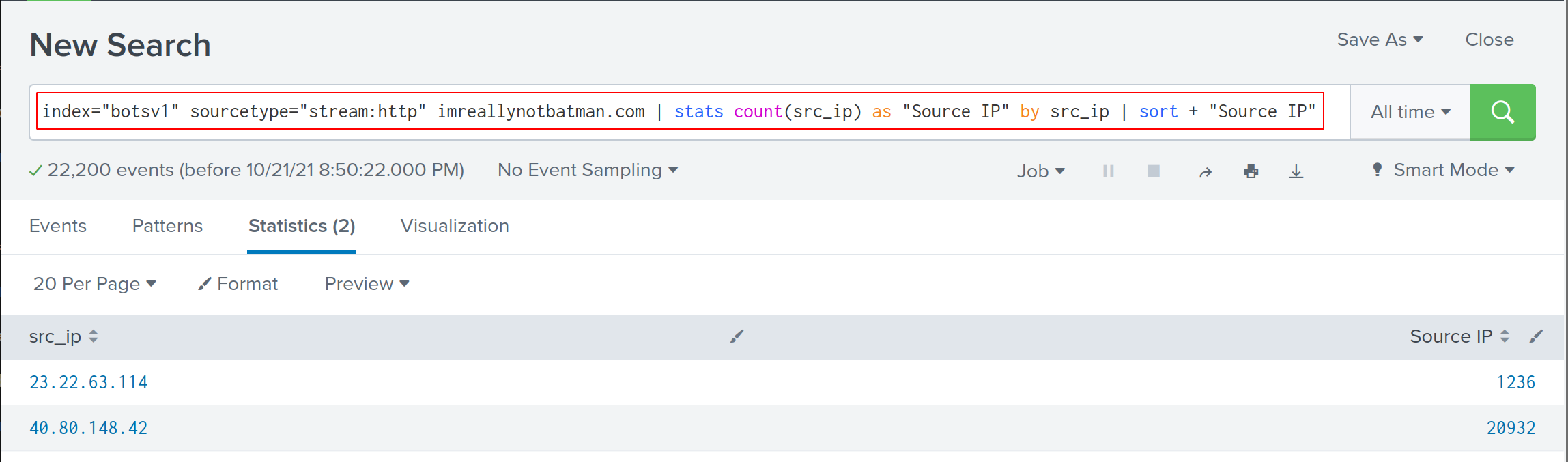
So far, we can safely deduce the 40.80.148.42 address is dubious. Now, let’s us further dig into those traffic by specifying suricata sourcetype.
The following query will give us a bird’s eye view of all suricata alerts against this address:
index="botsv1" sourcetype="suricata" src="40.80.148.42" | search event_type=alert | stats count(alert.signature) as "Alert" by alert.signature | sort - "Alert"
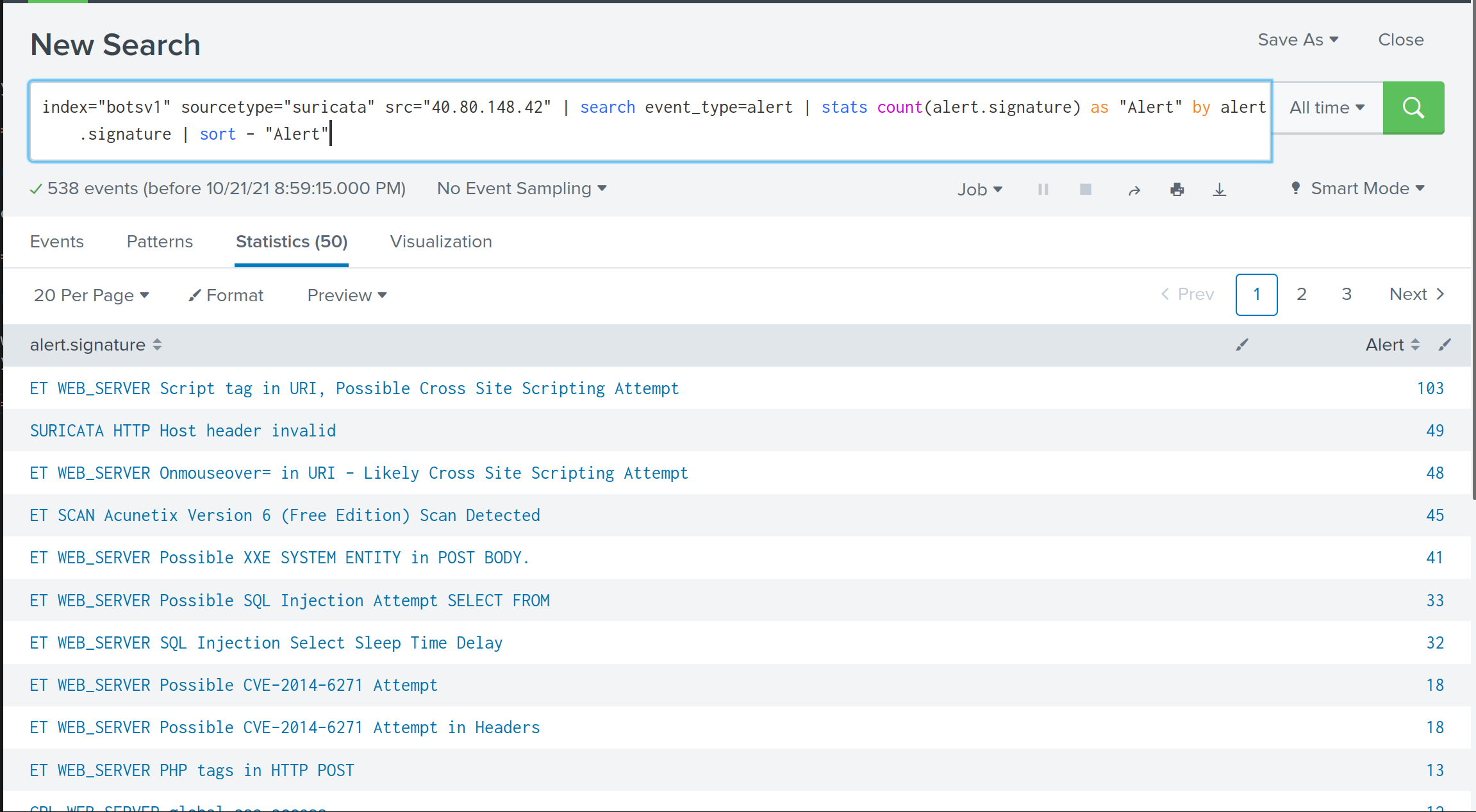
As we can see, multiple attacks are mounted by the APT group. Let’s look at one of the HTTP request being sent by this adversary. The search is as below:
index="botsv1" sourcetype="stream:http" src="40.80.148.42"
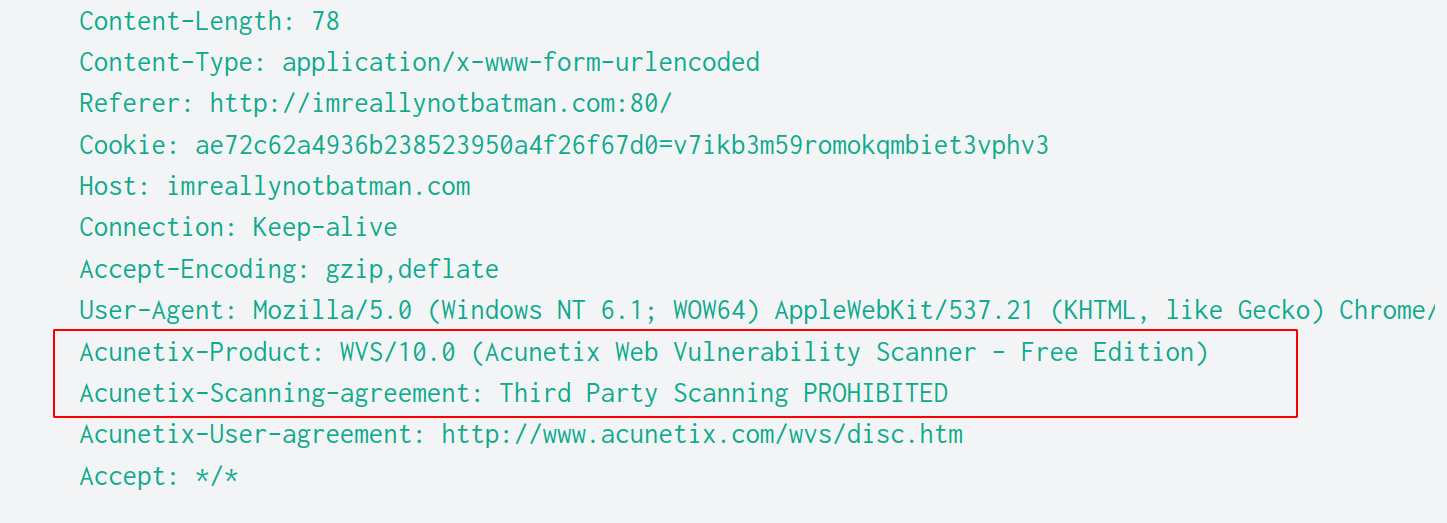
After the query is submitted, we scroll down a little. There is an interesting HTTP header indicating the existence of Acunetix vulnerability scanner being used.
If we are interested in victim IP addresses, we can do so by looking up the dest field. This field reveals us which IP address is targerted by the scanner.
SPL query to use is same as the previous one.
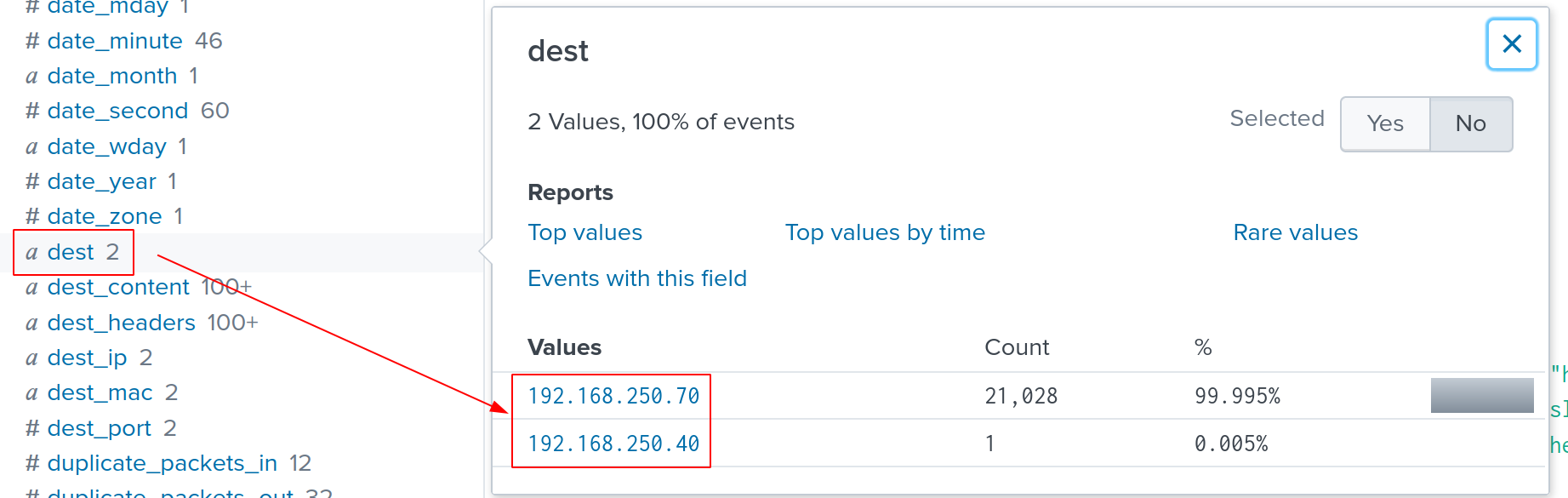
There are two IP addresses: 192.168.250.70 and 192.168.250.40. Obviously, 192.168.250.70 is the primary target, which is also the organization’s website.
If we want to look at HTTP URI being scanned by this APT group, we can filter the status of http stream:
index="botsv1" sourcetype="stream:http" status=200 src="40.80.148.42" dest="192.168.250.70" | stats count by uri | sort - count
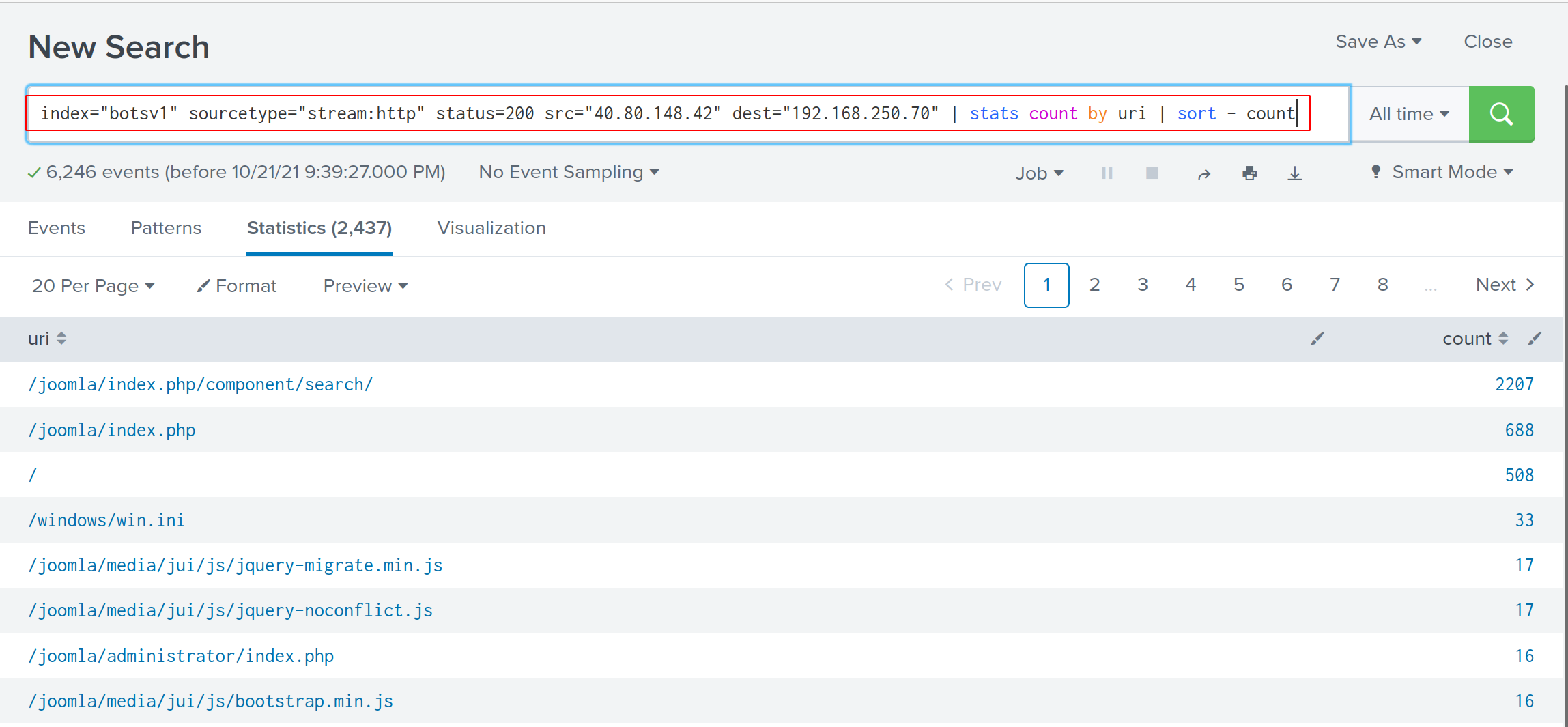
Others, we can further inspect the iis stream for more information:
index="botsv1" sourcetype="iis"
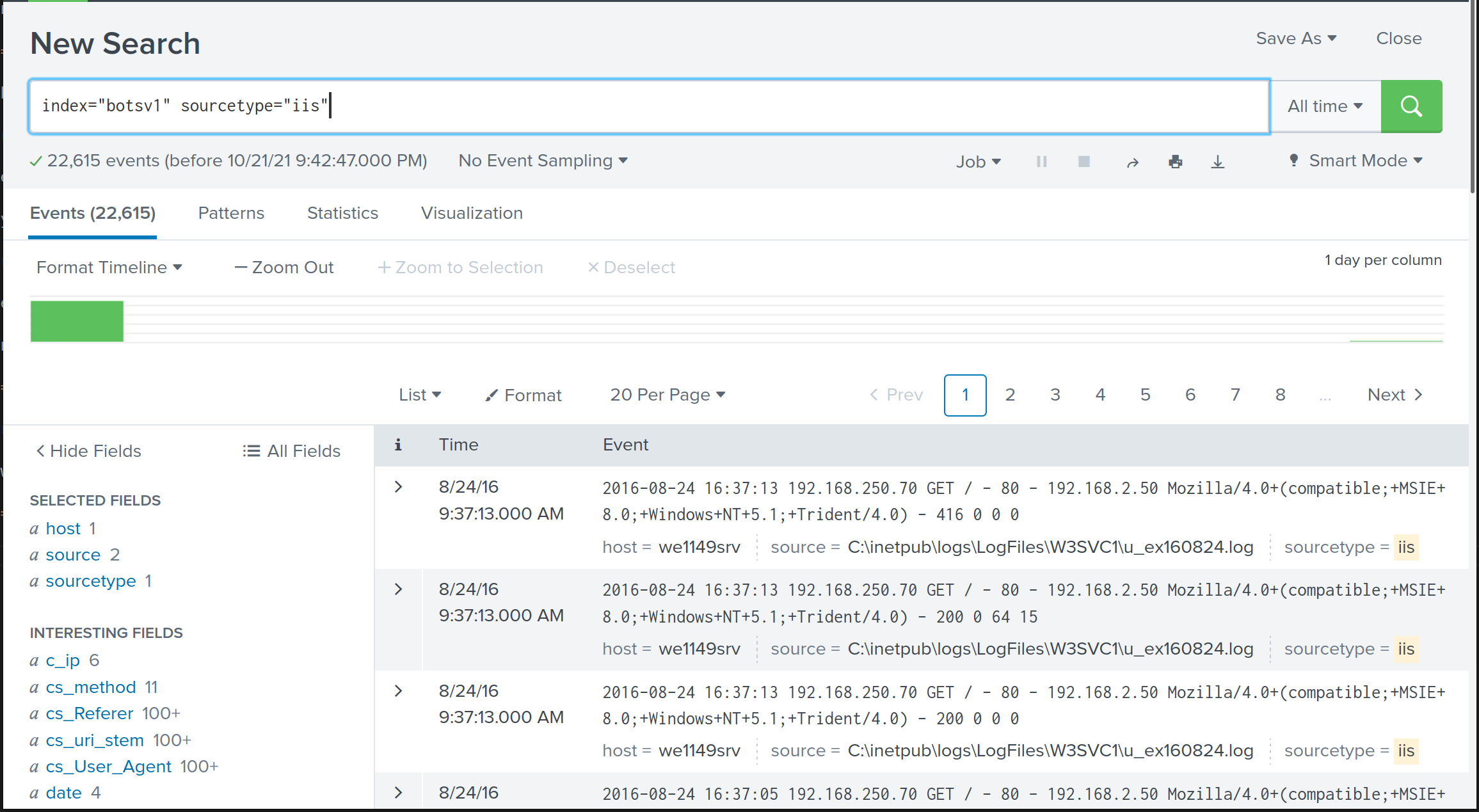
At this point, we can conclude that the APT group employed Acunetix vulnerability scanner to perform reconnaissance activities against the Joomla website hosted on 192.168.250.70.
Step 2 - Weaponization
In this phase, we’ll start investigating target’s infrastructure and all relevant information related to this APT.
Bearing with Splunk, we’re able to derive a relatively good amount of information from 40.80.148.42. Yet, applying same tatiics against the 23.22.63.114 address doesn’t yield us a lot of interesting information.
Now, if we go to the open source such as robtex, or threatcrowd and submit this ip address …
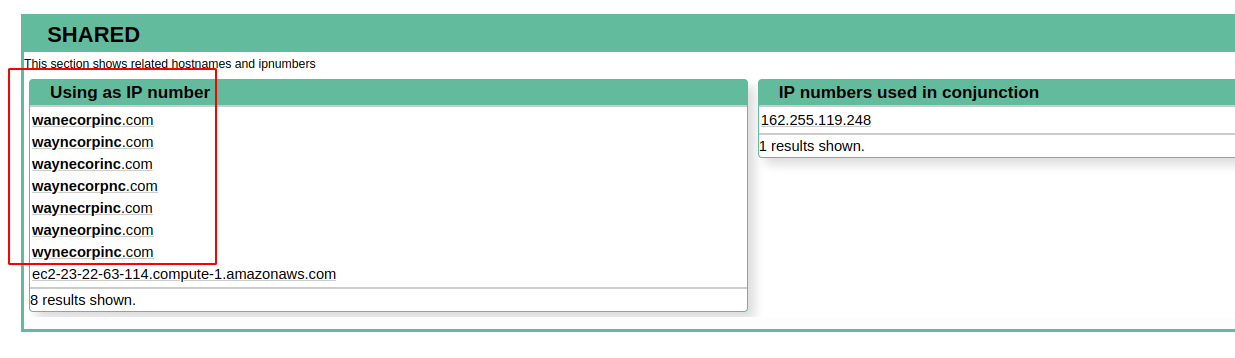
we can see that this IP address returns some phising domains, which are similar to Wayne Enterprise.
Besides, employing open source like ThreatCrowd also reveals us a good deal of information.
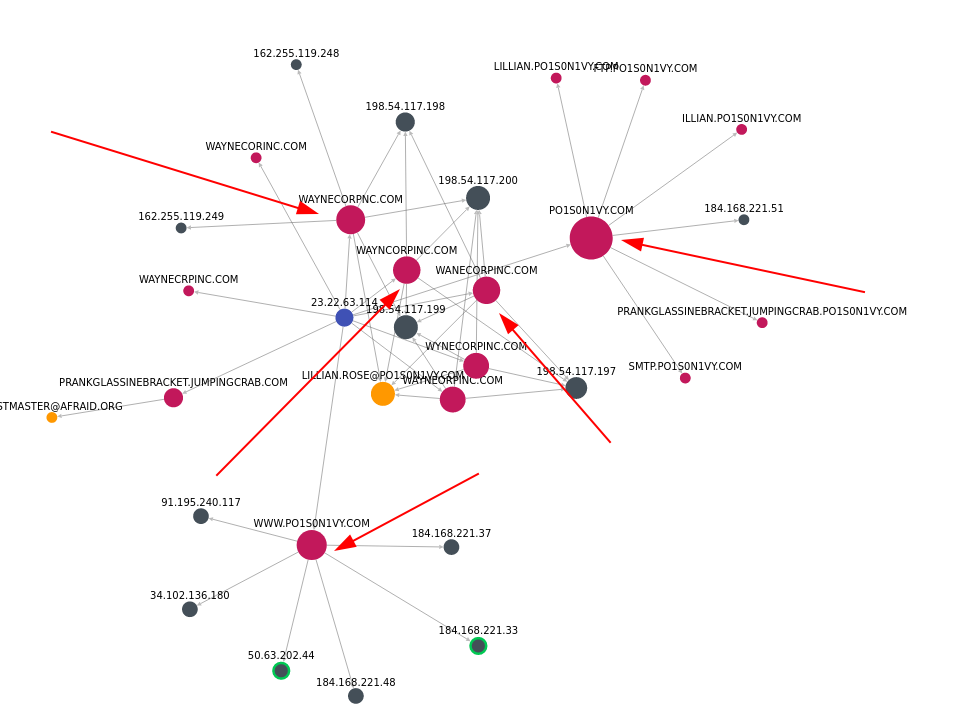
Furthermore, if we perform DNS lookup against one of the above phising domains, we’ll come across more valuable information i.e. Email or NS.
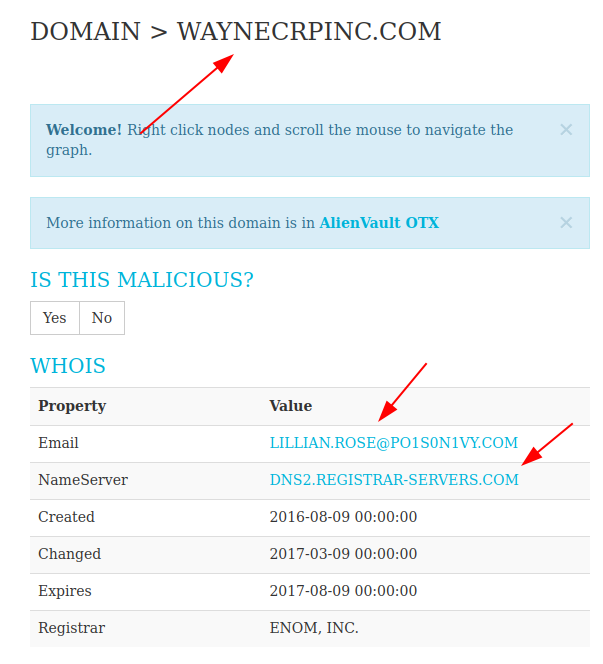
With the email, we can potentially divulge other infrastructure associated with the APT group.
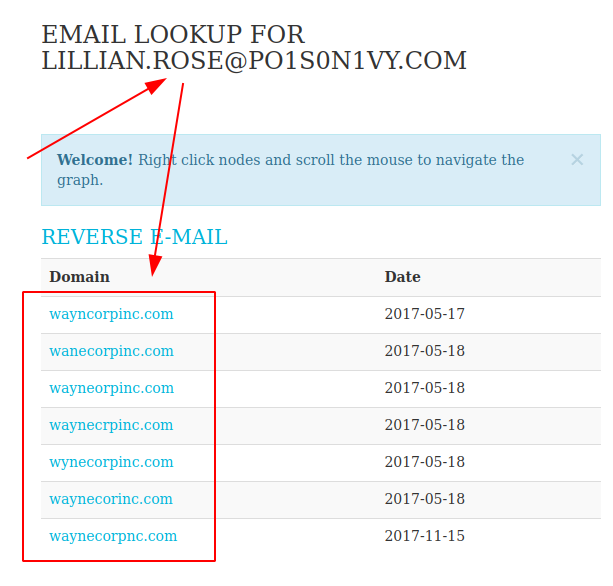
Step 3 - Delivery Activities
In this phase, we want to gather more information, potential malware used by the attackers …
Website such as ThreatMiner gives us precious information relating to TTPs used by the APT.
Submitting the 23.22.63.114 address to www.threatminer.org returns a few sample malwares being used by the adversaries …
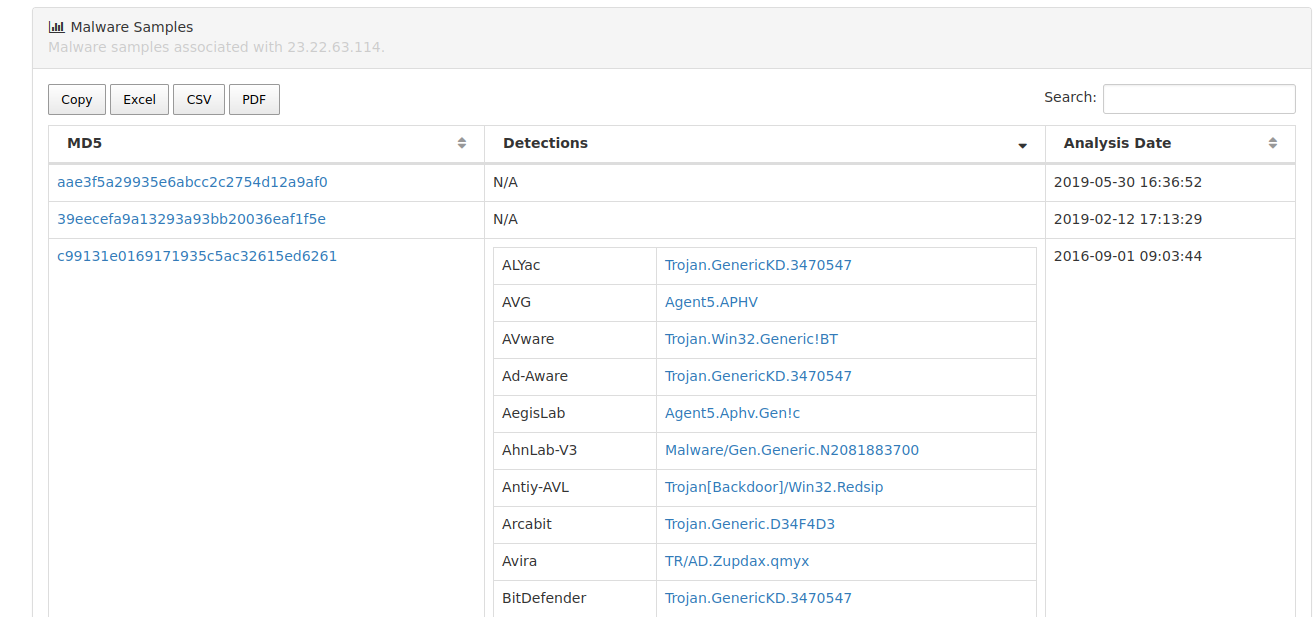
Again, if we submit MD5 hashes to open sources as VirusTotal or Hybrid Analysis, we can retrieve metadata about those samples, which is useful in the future investigation.
Next post: we’ll examine Exploitation, Installation, and C2 phases used by the APT.